MBA - 106: e-Business
E-BUSINESS,
TYPES OF E-BUSINESS & E-BUSINESS IN INDIA
E-business
is broader than e-commerce; including the transaction based e-commerce
businesses and those who run traditionally but cater to online activities as
well. An e-business can run any portion of its internal processes online,
including inventory management, risk management, finance, human resources. For
a business to be e-commerce and e-business, it must both sell products online
and handle other company activities or additional sales offline.
E-Business
in addition to encompassing E-commerce includes both front and back-office
applications that form the engine for modern E-commerce. E-business is not just
about E-commerce transactions; it's about re-defining old business models, with
the aid of technology to maximize customer value. E-Business is the overall
strategy and E-commerce is an extremely important facet of E-Business.
Thus
e-business involves not merely setting up the company website and being able to
accept credit card payments or being able to sell products or services on time.
It involves fundamental re-structuring and streamlining of the business using
technology by implementing enterprise resource planning (ERP) systems, supply
chain management, customer relationship management, data ware housing, data
marts, data mining, etc.
While
many people use e-commerce and e-business interchangeably, they aren't the
same, and the differences matter to businesses in today's economy. The
"e" is short for "electronic" or "electronic
network," and both words apply to business that utilizes electronic
networks to conduct their commerce and other business activities. In the same
way that all squares are rectangles, but not all rectangles are squares, all
e-commerce companies are e-businesses, but not vice versa.
There are four
main categories: B2B, B2C, C2B, and C2C:
B2B
(Business to Business) — this kind of e-commerce involves companies doing
business with each other. One example is manufacturers selling to distributors
and wholesalers selling to retailers.
B2C
(Business to Consumer) — this is what most people think of when they hear
"e-commerce." B2C consists of businesses selling to the general
public through shopping cart software, without needing any human interaction.
An example of this would be Amazon.
C2B
(Consumer to Business) — in this scenario, a consumer would post a project
with a set budget online, and companies bid on the project. The consumer reviews the bids and selects the
company — Elance is an example of this.
C2C
(Consumer to Consumer) — this type of e-commerce is made up of online
classifieds or forums where individuals can buy and sell their goods, thanks to
systems like PayPal. An example of this would be eBay.
E-commerce in
India
India
is at the cusp of a digital revolution. Declining broadband subscription
prices, aided by the launch of 4G services, have been driving this trend. This
has led to an ever-increasing number of “netizens.” Furthermore, the recent
launch of 4G services is expected to significantly augment the country’s
internet user base.
Internet
has become an integral part of this growing population segment for remaining
connected with friends, accessing emails, buying movie tickets and ordering
food. The changing lifestyles of the country’s urban population have also led
many people relying on the internet for their shopping needs. The convenience
of shopping from the comfort of one’s home and having a wide product assortment
to choose from has brought about increased reliance on the online medium.
The
trend of online shopping is set to see greater heights in coming years, not
just because of India’s rising internet population, but also due to changes in
the supporting ecosystem. Players have made intensive efforts to upgrade areas
such as logistics and the payment infrastructure. Furthermore, the Indian
consumer’s perception of online shopping has undergone a drastic change, and
only for the good. Given these developments, venture capital investors, who
were restricting themselves to the sidelines, are now taking a keen interest in
the country’s e-Commerce market.
The
e-Commerce market in India has enjoyed phenomenal growth of almost 50% in the
last five years. Although the trend of e-Commerce has been making rounds in
India for 15 years, the appropriate ecosystem has now started to fall in place.
The considerable rise in the number of internet users, growing acceptability of
online payments, the proliferation of internet-enabled devices and favourable
demographics are the key factors driving the growth story of e-Commerce in the
country. The number of users making online transactions has been on a rapid
growth trajectory, and it is expected to grow from 11 million in 2011 to 38
million by the end of 2016.
The
online retail segment has evolved and grown significantly over the past few
years. Cash-on-delivery has been one of the key growth drivers and is touted to
have accounted for 50% to 80% of online retail sales.
In
India, the e-commerce industry is a two-billion-dollar industry, which is a
fraction of the global industry size. But it is set to grow 10 times in the
next 10 years fuelled by increasing Internet and mobile penetration. At present
India’s Internet penetration stands only at 12 per cent as against China’s
30-plus per cent.
Web
business is powered by many departments, from digital marketing, logistics and
warehousing to call centres. There is also a need for business intelligence and
technology support professionals, multimedia specialists, researchers and,
especially, online fashion retailers like us also employ stylists,
merchandisers and photographers. The main challenge of being in this business
is that it is technology-driven. One needs to understand how people behave
online — consumer behaviour on the Internet. The industry is still at a nascent
stage and we can expect to see lots of innovation, especially in the marketing
and supply chain departments.
The
most unique aspect of online shopping is that you don’t see your customer. As
much as this offers a lot of ease to the shopper, it only makes the work of the
sellers more challenging. The store front is your website. Therefore, you need
to make sure that you are absolutely spot-on with the look and feel, ease of
navigation, technical stuff like loading time, etc.
Secondly,
you need to be advertising online first before heading offline. This leads to a
huge demand for digital marketing professionals, creative designers for
creating good Web banner ads. Finally, the fulfilment bit requires some experts
from the logistics industry to get the last mile right.
Every aspect of purchase,
customer service, processing is done via the web. This creates a lot of unique
profiles like merchandising officers and online marketing specialists.
BENEFITS AND
BARRIERS OF E-BUSINESS
Benefits
of e-Business
E-Business can provide the
following benefits over non-electronic commerce:
▫ Reduced costs by reducing labour, reduced paper work,
reduced errors in keying in data, reduce post costs. E-business is one of the
cheapest means of doing business as it is e-business development that has made
it possible to reduce the cost of promotion of products and services.
▫ Reduced time: Shorter lead times for payment and
return on investment in advertising, faster delivery of product. E-Business
reduces delivery time and labour cost thus it has been possible to save the
time of both - the vendor and the consumer.
▫ Flexibility with efficiency: The ability to
handle complex situations, product ranges and customer profiles without the
situation becoming unmanageable. There is no time barrier in selling the
products. One can log on to the internet even at midnight and can sell the
products at a single click of mouse.
▫ Improve relationships with trading partners: Improved
communication between trading partners leads to enhanced long-term relationships.
▫ Lock in Customers: The closer you are to your
customer and the more you work with them to change from normal business
practices to best practice e-business the harder it is for a competitor to
upset your customer relationship. The on-time alerts are meant for the
convenience of the consumers and inform the consumers about new products.
▫ New Markets: The Internet has the potential to
expand your business into wider geographical locations.
Barriers
of e-Business
▫ E-Business Lacks That Personal Touch: Not that all
physical retailers have a personal approach, but I do know of several retailers
who value human relationship. As a result, shopping at those retail outlets is
reassuring and refreshing. Clicking on "Buy Now," and piling up
products in virtual shopping carts, is just not the same for me. Different
people sing to different tunes.
▫ E-Business Delays Goods: Unless you are
using a website to merely order a pizza online, ecommerce websites deliver take
a lot longer to get the goods into your hands. Even with express shipping, the
earliest you get goods is "tomorrow." But if you want to buy a pen because
you need to write something right now, you cannot buy it off an ecommerce
website. Likewise with candy that you want to eat now, a book that you want to
read tonight, a birthday gift that you need this evening. An exception to this
rule is in the case of digital goods, e.g. an e-book or a music file. In this
case, ecommerce might actually be faster than purchasing goods from a physical
store.
▫ Many Goods Cannot Be Purchased Online: Despite its
many conveniences, there are goods that you cannot buy online. Most of these
would be in the categories of "perishable" or "odd-sized."
Think about it, you cannot order a Popsicle (also referred to as an ice pop or
ice lolly) or a dining table set. Likewise, a dining table set can certainly be
purchased online. In some cases, the cost of logistics is bearable. But if you
have to return the furniture, you will get well-acquainted with the
inconvenience of ecommerce.
▫ E-Business Does Not Allow You to Experience the
Product before Purchase: You cannot touch the fabric of the garment you want
to buy. You cannot check how the shoe feels on your feet. You cannot
"test" the perfume that you want to buy. In many cases, customers
want to experience the product before purchase. E-Business does not allow that.
If you buy a music system, you cannot play it online to check if it sounds
right? If you are purchasing a home-theatre system, you would much rather sit
in the "experience centre" that several retail stores set up.
▫ Anyone can set up an E-Business Website: We live in an
era where online storefront providers bring you the ability to set up an
ecommerce store within minutes. But if anybody can set up a store, how do I
know that the store I am purchasing from is genuine? The lowered barriers to
entry might be a great attraction to the aspiring ecommerce entrepreneur. But
for the buyer, reliability can be an issue. This could lead customers to
restrict their online purchases to famous ecommerce websites.
▫ Security: When making an online purchase, you
have to provide at least your credit card information and mailing address. In
many cases, ecommerce websites are able to harvest other information about your
online behaviour and preferences. This could lead to credit card fraud, or
worse, identity theft.
BUSINESS MODEL
AND THE KEY ELEMENTS OF A BUSINESS MODEL
A
business model is a set of planned activities (sometimes referred to as
business processes) designed to result in a profit in a marketplace. A business
model is not always the same as a business strategy although in some cases they
are very close insofar as the business model explicitly takes into account the
competitive environment. The business model is at the center of the business
plan. A business plan is a document that describes a firm’s business model. A
business plan always takes into account the competitive environment. An
e-commerce business model aims to use and leverage the unique qualities of the
Internet and the World Wide Web.
Eight key
elements of a Business model
If
you hope to develop a successful business model in any arena, not just
e-commerce, you must make sure that the model effectively addresses the eight
elements listed in Table 2.1 (next page). These elements are: value
proposition, revenue model, market opportunity, competitive environment,
competitive advantage, market strategy, organizational development, and
management team. Many writers focus on a firm’s value proposition and revenue
model. While these may be the most important and most easily identifiable
aspects of a company’s business model, the other elements are equally important
when evaluating business models and plans, or when attempting to understand why
a particular company has succeeded or failed.
Value
Proposition: A company’s value proposition is at the
very heart of its business model. A value proposition defines how a company’s
product or service fulfils the needs of customers. To develop and/or analyze a
firm’s value proposition, you need to understand why customers will choose to
do business with the firm instead of another company and what the firm provides
that other firms do not and cannot. From the consumer point of view, successful
e-commerce value propositions include: personalization and customization of
product offerings, reduction of product search costs, reduction of price
discovery costs, and facilitation of transactions by managing product delivery.
FreshDirect,
for instance, primarily is offering customers the freshest perishable food in
New York, direct from the growers and manufacturers, at the lowest prices,
delivered to their homes at night. Although local supermarkets can offer fresh
food also, customers need to spend an hour or two shopping at those stores
every week. Convenience and saved time are very important elements in
FreshDirect’s value proposition to customers.
Revenue
Model: A firm’s revenue
model describes how the firm will earn revenue, generate profits, and produce a
superior return on invested capital. We use the terms revenue model and
financial model interchangeably. The function of business organizations is both
to generate profits and to produce returns on invested capital that exceed
alternative investments. Profits alone are not sufficient to make a company
“successful”. In order to be considered successful, a firm must produce returns
greater than alternative investments. Firms that fail this test go out of
existence.
Retailers,
for example, sell a product, such as a personal computer, to a customer who
pays for the computer using cash or a credit card. This produces revenue. The
merchant typically charges more for the computer than it pays out in operating
expenses, producing a profit. But in order to go into business, the computer
merchant had to invest capital—either by borrowing or by dipping into personal
savings. The profits from the business constitute the return on invested
capital, and these returns must be greater than the merchant could obtain
elsewhere, say, by investing in real estate or just putting the money into a
savings account.
Market
Opportunity: The term market
opportunity refers to the company’s intended marketspace (i.e., an area of
actual or potential commercial value) and the overall potential financial
opportunities available to the firm in that marketspace. The market opportunity
is usually divided into smaller market niches. The realistic market opportunity
is defined by the revenue potential in each of the market niches where you hope
to compete. For instance, let’s assume you are analyzing a software training
company that creates software-learning systems for sale to corporations over the
Internet. The overall size of the software training market for all market
segments is approximately $70 billion. The overall market can be broken down,
however, into two major market segments: instructor-led training products,
which comprise about 70% of the market ($49 billion in revenue), and
computer-based training, which accounts for 30% ($21 billion). There are
further market niches within each of those major market segments, such as the
Fortune 500 computer-based training market and the small business
computer-based training market. Because the firm is a start-up firm, it cannot
compete effectively in the large business, computer-based training market
(about $15 billion). Large brand-name training firms dominate this niche. The
start-up firm’s real market opportunity is to sell to the thousands of small
business firms who spend about $6 billion on computer-based software training
and who desperately need a cost-effective training solution. This is the size
of the firm’s realistic market opportunity.
Competitive
Environment: A firm’s
competitive environment refers to the other companies selling similar products
and operating in the same market-space. It also refers to the presence of
substitute products and potential new entrants to the market, as well as the
power of customers and suppliers over your business. We discuss the firm’s
environment later in the chapter. The competitive environment for a company is
influenced by several factors: how many competitors are active, how large their
operations are, what the market share of each competitor is, how profitable
these firms are, and how they price their products.
Firms
typically have both direct and indirect competitors. Direct competitors are
those companies that sell products and services that are very similar and into
the same market segment. For example, Priceline and Travelocity, both of whom
sell discount airline tickets online, are direct competitors because both
companies sell identical products—cheap tickets. Indirect competitors are
companies that may be in different industries but still compete indirectly
because their products can substitute for one another. For instance, automobile
manufacturers and airline companies operate in different industries, but they
still compete indirectly because they offer consumers alternative means of
transportation. CNN.com, a news outlet, is an indirect competitor of ESPN.com
not because they sell identical products, but because they both compete for
consumers’ time online.
The
existence of a large number of competitors in any one segment may be a sign
that the market is saturated and that it may be difficult to become profitable.
On the other hand, a lack of competitors could either signal an untapped market
niche ripe for the picking or a market that has already been tried without success
because there is no money to be made. Analysis of the competitive environment
can help you decide which it is.
Competitive
Advantage: Firms achieve a
competitive advantage when they can produce a superior product and/or bring the
product to market at a lower price than most, or all, of their competitors
(Porter, 1985). Firms also compete on scope. Some firms can develop global
markets, while other firms can only develop a national or regional market.
Firms that can provide superior products at lowest cost on a global basis are
truly advantaged.
Firms
achieve competitive advantages because they have somehow been able to obtain
differential access to the factors of production that are denied to their
competitors—at least in the short term (Barney, 1991). Perhaps the firm has
been able to obtain very favourable terms from suppliers, shippers, or sources
of labour. Or perhaps the firm has more experienced, knowledgeable, and loyal
employees than any competitors. Maybe the firm has a patent on a product that others
cannot imitate, or access to investment capital through a network of former
business colleagues or a brand name and popular image that other firms cannot
duplicate. An asymmetry exists whenever one participant in a market has more
resources—financial backing, knowledge, information, and/or power—than other
participants. Asymmetries lead to some firms having an edge over others,
permitting them to come to market with better products, faster than
competitors, and sometimes at lower cost.
For
instance, when Steven Jobs, CEO and founder of Apple Computer, announced
iTunes, a new service offering legal, downloadable individual song tracks for
99 cents a tune that would be playable on Apple iPods or Apple desktops, the
company was given better than average odds of success simply because of Apple’s
prior success with innovative hardware designs, and the large stable of music
labels which Apple had meticulously lined up to support its online music
catalogue. Few competitors could match the combination of cheap, legal songs
and powerful hardware to play them on.
One
rather unique competitive advantage derives from being first mover. A
first-mover advantage is a competitive market advantage for a firm that results
from being the first into a marketplace with a serviceable product or service.
If first movers develop a loyal following or a unique interface that is
difficult to imitate, they can sustain their first-mover advantage for long
periods. Amazon provides a good example. However, in the history of technology-driven
business innovation, most first movers lack the complimentary resources needed
to sustain their advantages, and often follower firms reap the largest rewards.
Indeed, many of the success stories we discuss in this book are those of
companies that were slow followers—businesses that gained knowledge from
failure of pioneering firms and entered into the market late.
Companies
are said to leverage their competitive assets when they use their competitive
advantages to achieve more advantage in surrounding markets. For instance,
Amazon’s move into the online grocery business leverages the company’s huge
customer database and years of e-commerce experience.
Market
Strategy: No matter how
tremendous a firm’s qualities, its marketing strategy and execution are often
just as important. The best business concept, or idea, will fail if it is not
properly marketed to potential customers.
Everything
you do to promote your company’s products and services to potential customers
is known as marketing. Market strategy is the plan you put together that
details exactly how you intend to enter a new market and attract new customers.
Part of FreshDirect’s strategy, for instance, is to develop close supply chain
partnerships with growers and manufacturers so it purchases goods at lower
prices directly from the source. This helps FreshDirect lower its prices for
consumers.
By
partnering with suppliers that could benefit from FreshDirect’s access to
consumers, FreshDirect is attempting to extend its competitive advantages. YouTube
and PhotoBucket have a social network marketing strategy which encourages users
to post their content on the sites for free, build personal profile pages,
contact their friends, and build a community. In these cases, the customer is
the marketing staff!
Organizational
Development: Although many
entrepreneurial ventures are started by one visionary individual, it is rare
that one person alone can grow an idea into a multi-million dollar company.
In
most cases, fast-growth companies—especially e-commerce businesses—need
employees and a set of business procedures. In short, all firms—new ones in
particular—need an organization to efficiently implement their business plans
and strategies. Many e-commerce firms and many traditional firms who attempt an
e-commerce strategy have failed because they lacked the organizational
structures and supportive cultural values required to support new forms of
commerce.
Companies
that hope to grow and thrive need to have a plan for organizational development
that describes how the company will organize the work that needs to be
accomplished. Typically, work is divided into functional departments, such as
production, shipping, marketing, customer support, and finance. Jobs within
these functional areas are defined, and then recruitment begins for specific
job titles and responsibilities. Typically, in the beginning, generalists who
can perform multiple tasks are hired. As the company grows, recruiting becomes
more specialized.
For
instance, at the outset, a business may have one marketing manager. But after
two or three years of steady growth, that one marketing position may be broken
down into seven separate jobs done by seven individuals.
Management
Team: Arguably, the
single most important element of a business model is the management team
responsible for making the model work. A strong management team gives a model
instant credibility to outside investors, immediate market-specific knowledge,
and experience in implementing business plans. A strong management team may not
be able to salvage a weak business model, but the team should be able to change
the model and redefine the business as it becomes necessary.
Eventually,
most companies get to the point of having several senior executives or
managers. How skilled managers are, however, can be a source of competitive
advantage or disadvantage. The challenge is to find people who have both the
experience and the ability to apply that experience to new situations.
To be able to identify good
managers for a business start-up, first consider the kinds of experiences that
would be helpful to a manager joining your company. What kind of technical
background is desirable? What kind of supervisory experience is necessary? How
many years in a particular function should be required? What job functions
should be fulfilled first: marketing, production, finance, or operations?
Especially in situations where financing will be needed to get a company off
the ground, do prospective senior managers have experience and contacts for
raising financing from outside investors?
VALUE CHAINS IN
E-COMMERCE AND VALUE CHAIN AREAS
A value chain for a product is
the chain of actions that are performed by the business to add value in
creating and delivering the product. For example, when you buy a product in a store
or from the web, the value chain includes the business selecting products to be
sold, purchasing the components or tools necessary to build them from a
wholesaler or manufacturer, arranging the display, marketing and advertising
the product, and delivering the product to the client.
In the book ‘Designing Systems for Internet Commerce’ by G. Winfield Treese and
Lawrence C. Stewart, the authors suggest breaking down the aspects of your
business into four general value-chain areas:
§ Attract-in which you get and keep customer
interest, and includes advertising and marketing
§ Interact-in which you turn interest into orders,
and includes sales and catalogues
§ Act-in which you manage orders, and
includes order capture, payment, and fulfilment
§ React-in which you service customers, and
includes technical support, customer service, and order tracking
Value
Proposition
The value proposition describes
the value that the company will provide to its customers and, sometimes, to
others as well. With a value proposition the company attempts to offer better
value than competitors so that the buyer will benefit most with this product.
A value proposition may include
one or more of the following points:
§ Reduced price
§ Improved service
or convenience such as the "1 click" checkout
§ Speed of
delivery and assistance
§ Products that
lead to increased efficiency and productivity
§ Access to a
large and available inventory that presents options for the buyer
Providing value in an e-business
uses the same approach as providing value in any business, although it may
require different capabilities. But common to both are the customers who seek
out value in a business transaction. The value proposition helps focus the
business on the well-being of the customer, where it remains in successful companies.
Value
Delivery through Integration of Activities
Integration of Organization or
Enterprise Operations
The integration of systems inside
and outside the organization can provide value for both customers and the
organization. One of the requirements for e-business is to link front-end with
back-end systems in order to automate the online operations of the
organization.
Front-end activities deal
directly with the customer while back-end systems include all of the internal
support activities that do not deal directly with the customer. Some
enterprises have different geographic locations for front-end and back-end
office activities and rely on the integration of the associated computer and
network systems for successful corporate operations.
ELECTRONIC DATA INTERCHANGE: ITS
BENEFITS, PROCESS AND COMPONENTS
Electronic
Data Interchange (EDI) is the computer-to-computer exchange
of business documents in a standard electronic format between business
partners.
By
moving from a paper-based exchange of business document to one that is
electronic, businesses enjoy major benefits such as reduced cost, increased
processing speed, reduced errors and improved relationships with business
partners.
Technically,
EDI is a set of standards that define common formats for the information so it
can be exchanged in this way.
Each term in the definition is significant:
▫ Computer-to-computer– EDI replaces postal
mail, fax and email. While email is also an electronic approach, the documents
exchanged via email must still be handled by people rather than computers.
Having people involved slows down the processing of the documents and also
introduces errors. Instead, EDI documents can flow straight through to the
appropriate application on the receiver’s computer (e.g. the Order Management
System) and processing can begin immediately.
A typical manual process looks like this, with lots of paper and people involvement:
The EDI process looks like this – no paper, no
people involved:
▫ Business documents – These are any of the documents that are typically exchanged
between businesses. The most common documents exchanged via EDI are purchase
orders, invoices and Advance Ship Notices. But there are many, many others such
as bill of lading, customs documents, inventory documents, shipping status
documents.
▫ Standard format– Because EDI documents must be processed by computers rather than
humans, a standard format must be used so that the computer will be able to
read and understand the documents. A standard format describes what each piece
of information is and in what format (e.g. integer, decimal, mmddyy). Without a
standard format, each company would send documents using its company-specific
format and, much as an English-speaking person probably doesn’t understand
Japanese, the receiver’s computer system doesn’t understand the
company-specific format of the sender’s format. There are several EDI standards
in use today, including ANSI, EDIFACT, TRADACOMS and XML. And, for each
standard there are many different versions, e.g. ANSI 5010 or EDIFACT version
D12, Release A. When two businesses decide to exchange EDI documents, they must
agree on the specific EDI standard and version. Businesses typically use an EDI
translator – either as in-house software or via an EDI service provider – to
translate the EDI format so the data can be used by their internal applications
and thus enable straight through processing of documents.
▫ Business partners – The exchange of EDI documents is typically between two different
companies, referred to as business partners or trading partners. For example,
Company A may buy goods from Company B. Company A sends orders to Company B.
Company A and Company B are business partners.
EDI – the Process
There
are 3 steps to sending EDI documents – Prepare the documents, Translate the
documents into EDI format, Transmit the EDI documents to your partner.
Step 1: Prepare the documents to be sent
The
first step is to collect and organize the data. For example, instead of
printing a purchase order, your system creates an electronic file with the
necessary information to build an EDI document. The sources of data and the
methods available to generate the electronic documents can include:
§ Human data entry via screens
§ Exporting PC-based data from spreadsheets or databases
§ Reformatted electronic reports into data files
§ Enhancing existing applications to automatically create output files
that are ready for translation into an EDI standard
§ Purchasing application software that has built-in interfaces for EDI
files
Step 2: Translate the documents into EDI format
The
next step is to feed your electronic data through translator software to
convert your internal data format into the EDI standard format using the
appropriate segments and data elements. You can purchase EDI translation
software that you manage and maintain on your premises. This requires
specialized mapping expertise in order to define how your internal data is to
be mapped (i.e. correlated) to the EDI data. Translation software is available
to suit just about any computing environment and budget, from large systems
that handle thousands of transactions daily to PC-based software that need only
process a few hundred transactions per week.
Alternatively,
you can use the translation services of an EDI service provider. In that case,
you send your data to the provider, who handles translation to and from the EDI
format on your behalf.
Step 3: Connect and transmit your EDI documents to
your business partner
Once
your business documents are translated to the appropriate EDI format they are
ready to be transmitted to your business partner. You must decide how you will
connect to each of your partners to perform that transmission. There are
several ways, the most common of which include 1) to connect directly using AS2
or another secure internet protocol, 2) connect to an EDI Network provider
(also referred to as a VAN provider) using your preferred communications
protocol and rely on the network provider to connect to your business partners
using whatever communications protocol your partners prefer, or 3) a
combination of both, depending on the particular partner and the volume of
transactions you expect to exchange.
EDI – the Benefits
For
many companies, EDI is really not a choice. It may be a requirement of doing business
with larger organizations, including big retailers, manufacturers and
government agencies.
Once
you are communicating via EDI, the door is open to maximizing its value to your
business. By integrating your EDI workflow with your back-end business or
accounting system, you can streamline the entire process of how information
flows through your organization. The benefits can be tremendous, including:
§ Lower costs – By reducing the manual keying
of data, handling of documents and other processes, you can potentially reduce
the costs of labour and paper, and reduce errors (and their associated costs).
§ Higher efficiency – Sending and receiving EDI data
happens in seconds, and the information can be acted on immediately. This means
time savings for you and your trading partners.
§ Improved accuracy – You can reduce errors by using
EDI because manual and duplicate entry is eliminated. Everything flows
untouched, leaving a trail for easy future tracking.
§ More supply chain
visibility – With EDI,
product sales data, product inventory status, demand forecasts and other
metrics can be shared with suppliers and their suppliers. This allows for
better inventory management and supports just-in-time delivery.
§ Enhanced security – Thanks to numerous
communications protocols addressing encryption and other security issues,
critical business or personal data may be exchanged with higher levels of
security via EDI than by any other means.
§ Greater management
information – Because
EDI data is electronic data, you have a source of information to guide
management decisions or to mine for further analysis.
The
process improvements that EDI offers are significant and can be dramatic. For
example, consider the difference between the traditional paper purchase order
and its electronic counterpart:
A Traditional Document Exchange of a Purchase Order
§ This process normally
takes between three and five days.
§ Buyer makes a buying
decision, creates the purchase order and prints it.
§ Buyer mails the purchase
order to the supplier.
§ Supplier receives the
purchase order and enters it into the order entry system.
§ Buyer calls supplier to
determine if purchase order has been received, or supplier mails buyer an
acknowledgment of the order.
An EDI Document Exchange of a Purchase Order
§ Buyer makes a buying
decision, creates the purchase order but does not print it.
§ EDI software creates an
electronic version of the purchase order and transmits it automatically to the
supplier.
§ Supplier's order entry
system receives the purchase order and updates the system immediately on
receipt.
§ Supplier's order entry
system creates an acknowledgment and transmits it back to confirm receipt.
This
process normally occurs overnight and can take less than an hour.
EDI – the components
Since
EDI started to get popular it has been many years and during all this time,
there were many EDI Software packages out there allowing companies to use EDI
easily.
In an
EDI Software there are couples of components that are crucial to the success of
the EDI Software solution in the organization. In this article we focus on some
of the main components that every EDI software package must have in order to
offer the user a positive experience and actually be used by company EDI
Administrator or one of the company advanced user who is in charge of the EDI
transactions, sending and receiving and the whole process involved in it.
§ Mapping
§ Translation
§ Validation
§ Import/Export
§ Reporting
§ Documents Turn Around
§ Monitoring and Alerting
EDI Mapping
EDI
mapping a process through which EDI data is translated to a format that is more
easily used in new environments. Through EDI Mapping you can, for example,
translate EDI messages into ASCII formats like flat-file, XML and other similar
forms.
EDI Translation
An EDI
Translator is also referred to as EDI software, or EDI translation
software. An EDI Translator provides a means of transforming EDI data to
and from formats suited for the enterprise. In other words, an EDI
Translator converts data from irregular, enterprise-specific forms into an ordered
and standardized structure that is compliant with EDI standards. The EDI
Translator also performs the same function in reverse, converting an EDI
document into a data structure that is appropriate for the enterprise. An
EDI Translator can be developed in house, or it can be purchased through third
party EDI Translator providers.
EDI Validation
EDI
Validation is the process of making sure that all the data in the EDI file are
correct, sitting in the appropriate location, that mandatory elements are not
missing and that element that are from a list of possible value for that
specific dictionary id, are correct.
The
file in the right format and follow the guidelines of the EDI Version and
standard.
Because
computers do not have the flexibility of reading and translating documents like
humans do, it is important to have a standard file format in EDI so that
computers can read and translate EDI documents correctly. It is also just
as important for users who are processing EDI files to adhere to the EDI
standard. One method of enforcing the EDI standard is to validate any
incoming EDI documents before they get translated. Validation not only
ensures a more accurate EDI translation, but also ensures a more robust
automated process by detecting and rejecting EDI files with anomalies that
could break the translation program and interrupt production.
EDI Import and EDI Export
EDI
Import and EDI Export is the process of importing data from a text file/excel
file or any other file format used by the organization into EDI file structure,
export is the same but the other way around. This option is vital in case the
user need some interface with his/her ERP software and many of those ERP
software packages have Import/Export routings, so in order to integrate between
the two software packages, the user can import and export data between the ERP
and the EDI software packages.
EDI Reporting
EDI
Reporting is the option to view reports on the transactions activity on a given
time frame. That way an EDI Administrator can see how many EDI Transactions
went through, how many of each document type, how many were with errors and
more.
Each
EDI software has its own set of EDI Reports, but the main point is that it has
to give the EDI Administrator some tools to look at the EDI Activity in the
organization so he can determine on what type of action to take in different
situation, for example if he receive too many transactions with errors.
EDI Documents Turn Around
EDI
Documents Turn Around is the part when user takes an EDI document like Purchase
Order (850, 875) and creates an Invoice of it, saving the user time and typing
errors.
SECURITY ISSUES
OF E-COMMERCE AND ELECTRONIC COMMERCE THREATS
The Internet and e-Commerce are
becoming a more and more popular sources for people to carry out their
shopping. The e-Commerce refers to the exchange of goods and services over the
Internet. This shopping covers everything from groceries to large electronic
goods and even cars. The rapid evolution of computing and communication
technologies and their standardizations have made the boom in e-Commerce
possible. Along with these there is also substantial growth in the areas of
credit card fraud and identity theft, by the very nature of it the internet is
a worldwide public network with thousands of millions of users. Amongst these
thousands of millions of users there is a percentage of those that are
described as crackers or hackers, it is these people that carry out the credit
card fraud and identity theft, there are numerous ways in which they do this
and many of these methods are facilitated with poor security on e-Commerce web
servers and in users computers.
Information security is the
protection against security threats that are defined as a circumstance,
condition, or event with the potential to cause economic hardship to data or
network resources in the form of destruction, disclosure, and modification of
data, denial of service, fraud, waste, and or abuse. Security has become one of
the most important issues that must be resolved first to ensure success of
e-Commerce. The first step toward reducing the risk of e-Commerce security
threats is to identify the vulnerable areas where security threats can happen.
The main vulnerable areas for an
e-Commerce are hardware security, software security, and environment security.
Hardware
security
includes any devices used in running the e-Commerce website like network
devices and servers. Protecting the network with a properly configured firewall
device that is only allowing ports needed for accessing the e-Commerce website
is an essential part of network security.
Software
security
includes any software used in running the e-Commerce website such as the
operating system, web server software and database software. The operating
system should be configured for security through the process of operating
system hardening. Software should be contently being kept updated as patches
are routinely released to fix holes in security.
Environment
security
is the area around the hardware running the e-Commerce website and includes
human resources. Secure physical access to network and server devices by using
fences, locks, or other methods. Network, server, and software access
credentials should be highly complex and well guarded. Once a staff member has
left the company or moved to a different position, remove all access privileges
for that person that is no longer needed.
E-Commerce security requirements
can be studied by examining the overall process, beginning with the consumer
and ending with the commerce server. Considering each logical link in the
“commerce chain”, the assets that must be protected to ensure secure e-commerce
include client computers, the messages travelling on the communication channel,
and the web and commerce servers – including any hardware attached to the
servers. While telecommunications are certainly one of the major assets to be
protected, the telecommunications links are not the only concern in computer
and e-commerce security. For instance, if the telecommunications links were
made secure but no security measures were implemented for either client
computers or commerce and web-servers, then no communications security would
exist at all.
Client
threats
Until the introduction of executable
web content, Web pages were mainly static. Coded in HTML, static pages could do
little more than display content and provide links to related pages with
additional information. However, the widespread use of active content has
changed this perception.
1. Active content: Active content refers to
programs that are embedded transparently in web pages and that cause action to
occur. Active content can display moving graphics, download and play audio, or
implement web-based spreadsheet programs. Active content is used in e-commerce
to place items one wishes to purchase into a shopping cart and to compute the
total invoice amount, including sales tax, handling, and shipping costs. The
best known active content forms are Java applets, ActiveX controls, JavaScript,
and VBScript.
Since
active content modules are embedded in web pages, they can be completely
transparent to anyone browsing a page containing them. Anyone can embed
malicious active content in web pages. This delivery technique, called a trojan
horse, immediately begins executing and taking actions that cause harm.
Embedding active content to web pages involved in e-commerce introduces several
security risks. Malicious programs delivered quietly via web pages could reveal
credit card numbers, usernames, and passwords that are frequently stored in
special files called cookies. Because the internet is stateless and cannot
remember a response from one web page view to another, cookies help solve the
problem of remembering customer order information or usernames or passwords.
Malicious active content delivered by means of cookies can reveal the contents
of client-side files or even destroy files stored on client computers.
2. Malicious codes: Computer viruses, worms and
trojan-horses are examples of malicious code. A trojan horse is a program which
performs a useful function, but performs an unexpected action as well. Virus is
a code segment which replicates by attaching copies to existing executables. A
worm is a program which replicates itself and causes execution of the new copy.
These can create havoc on the client side.
3. Server-side masquerading: Masquerading
lures a victim into believing that the entity with which it is communicating is
a different entity. For example, if a user tries to log into a computer across
the internet but instead reaches another computer that claims to be the desired
one, the user has been spoofed. This may be a passive attack (in which the user
does not attempt to authenticate the recipient, but merely accesses it), but it
is usually an active attack (in which the masquerader issues responses to
mislead the user about its identity).
Communication
channel threats
The internet serves as the
electronic chain linking a consumer (client) to an e-commerce resource
(commerce server). Messages on the internet travel a random path from a source
node to a destination node. The message passes through a number of intermediate
computers on the network before reaching the final destination. It is
impossible to guarantee that every computer on the internet through which
messages pass is safe, secure, and non-hostile.
1. Confidentiality threats: Confidentiality
is the prevention of unauthorized information disclosure. Breaching
confidentiality on the internet is not difficult. Suppose one logs on to a
website – say www.anybiz.com – that contains a form with text boxes for name,
address, and e-mail address. When one fills out those text boxes and clicks the
submit button, the information is sent to the web-server for processing. One
popular method of transmitting data to a web-server is to collect the text box
responses and place them at the end of the target server’s URL. The captured
data and the HTTP request to send the data to the server is then sent. Now,
suppose the user changes his mind, decides not to wait for a response from the
anybiz.com server, and jumps to another website instead – say
www.somecompany.com. The server somecompany.com may choose to collect web
demographics and log the URL from which the user just came (www.anybiz.com). By
doing this, somecompany.com has breached confidentiality by recording the
secret information the user has just entered.
2. Integrity threats: An integrity threat exists when
an unauthorized party can alter a message stream of information. Unprotected
banking transactions are subject to integrity violations. Cyber vandalism is an
example of an integrity violation. Cyber vandalism is the electronic defacing
of an existing website page. Masquerading or spoofing – pretending to be
someone you are not or representing a website as an original when it really is
a fake – is one means of creating havoc on websites. Using a security hole in a
domain name server (DNS), perpetrators can substitute the address of their
website in place of the real one to spoof website visitors. Integrity threats
can alter vital financial, medical, or military information. It can have very
serious consequences for businesses and people.
3. Availability threats: The purpose of
availability threats, also known as delay or denial threats, is to disrupt
normal computer processing or to deny processing entirely. For example, if the
processing-speed of a single ATM machine transaction slows from one or two
seconds to 30 seconds, users will abandon ATM machines entirely. Similarly,
slowing any internet service will drive customers to competitors’ web or
commerce sites.
Server
threats
The server is the third link in
the client-internet-server trio embodying the e-commerce path between the user
and a commerce server. Servers have vulnerabilities that can be exploited by
anyone determined to cause destruction or to illegally acquire information.
1. Web-server threats: Web-server
software is designed to deliver web pages by responding to HTTP requests. While
web-server software is not inherently high-risk, it has been designed with web
service and convenience as the main design goal. The more complex the software
is, the higher is the probability that it contains coding errors (bugs) and
security holes – security weaknesses that provide openings through which
evildoers can enter.
2. Commerce server threats: The commerce
server, along with the web-server, responds to requests from web browsers
through the HTTP protocol and CGI scripts. Several pieces of software comprise
the commerce server software suite, including an FTP server, a mail server, a
remote login server, and operating systems on host machines. Each of this
software can have security holes and bugs.
3. Database threats: E-commerce systems store user
data and retrieve product information from databases connected to the
web-server. Besides product information, databases connected to the web contain
valuable and private information that could irreparably damage a company if it
were disclosed or altered. Some databases store username/password pairs in a
non-secure way. If someone obtains user authentication information, then he or
she can masquerade as a legitimate database user and reveal private and costly
information.
4. Common gateway interface threats: A common
gateway interface (CGI) implements the transfer of information from a web-server
to another program, such as a database program. CGI and the programs to which
they transfer data provide active content to web pages. Because CGIs are
programs, they present a security threat if misused. Just like web-servers, CGI
scripts can be set up to run with their privileges set to high – unconstrained.
Defective or malicious CGIs with free access to system resources are capable of
disabling the system, calling privileged (and dangerous) base system programs
that delete files, or viewing confidential customer information, including
usernames and passwords.
5. Password hacking: The simplest attack against a
password-based system is to guess passwords. Guessing of passwords requires
that access to the complement, the complementation functions, and the authentication
functions be obtained. If none of these have changed by the time the password
is guessed, then the attacker can use the password to access the system.
ENCRYPTION, DECRYPTION AND CRYPTOGRAPHY
Data that can be read and
understood without any special measures is called plaintext or cleartext. The
method of disguising plaintext in such a way as to hide its substance is called
encryption. Encrypting plaintext
results in unreadable gibberish called ciphertext.
You use encryption to ensure that information is hidden from anyone for whom it
is not intended, even those who can see the encrypted data. The process of
reverting ciphertext to its original plaintext is called decryption.
Encryption is the conversion of data into seemingly random,
incomprehensible data. Its meaningless form ensures that it remains
unintelligible to everyone for whom it is not intended, even if the intended
have access to the encrypted data.
The only way to transform the
data back into intelligible form is to reverse the encryption (known as
decryption). Public Key Cryptography encryption and decryption is performed
with Public and Private Keys.
Keys
A key is a value that works with
a cryptographic algorithm to produce a specific ciphertext. Keys are basically really,
really, really big numbers. Key size is measured in bits; the number
representing a 1024-bit key is darn huge. In public key cryptography, the
bigger the key, the more secure the ciphertext.
While the public and private keys
are mathematically related, it’s very difficult to derive the private key given
only the public key; however, deriving the private key is always possible given
enough time and computing power. This makes it very important to pick keys of
the right size; large enough to be secure, but small enough to be applied
fairly quickly. Additionally, you need to consider who might be trying to read
your files, how determined they are, how much time they have, and what their
resources might be.
Public
Key and Private Keys
The Public key and Private
key-pair comprises of two uniquely related cryptographic keys (basically long
random numbers). Below is an example of a Public Key:
3048 0241 00C9 18FA CF8D EB2D
EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F
922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001
The Public Key is what its name
suggests - Public. It is made available to everyone via a publicly accessible
repository or directory. On the other hand, the Private Key must remain confidential
to its respective owner.
Because the key pair is
mathematically related, whatever is encrypted with a Public Key may only be
decrypted by its corresponding Private Key and vice versa.
For example, if Bob wants to send sensitive data to Alice, and wants to be sure that
only Alice may be able to read it, he will encrypt the data with Alice's Public
Key. Only Alice has access to her corresponding Private Key and as a result is
the only person with the capability of decrypting the encrypted data back into
its original form.
As only Alice has access to her Private Key, it is possible that only
Alice can decrypt the encrypted data. Even if someone else gains access to the
encrypted data, it will remain confidential as they should not have access to Alice's
Private Key.
Public Key Cryptography can therefore achieve
Confidentiality. However another important aspect of Public Key Cryptography is
its ability to create a Digital Signature.
Cryptography
Cryptography
is the science of using mathematics to encrypt and decrypt data. Cryptography
enables you to store sensitive information or transmit it across insecure
networks (like the Internet) so that it cannot be read by anyone except the
intended recipient.
A cryptographic algorithm, or
cipher, is a mathematical function used in the encryption and decryption
process. A cryptographic algorithm works in combination with a key—a word,
number, or phrase—to encrypt the plaintext. The same plaintext encrypts to
different ciphertext with different keys. The security of encrypted data is
entirely dependent on two things: the strength of the cryptographic algorithm
and the secrecy of the key. A cryptographic algorithm, plus all possible keys
and all the protocols that make it work comprise a cryptosystem such as PGP
(Pretty Good Privacy). Pretty Good Privacy (PGP) is a data encryption and
decryption computer program that provides cryptographic privacy and
authentication for data communication.
Public
Key Cryptography
Public key cryptography is an
asymmetric scheme that uses a pair of keys for encryption: a public key, which
encrypts data, and a corresponding private, or secret key for decryption. You
publish your public key to the world while keeping your private key secret.
Anyone with a copy of your public key can then encrypt information that only
you can read.
It is computationally infeasible
to deduce the private key from the public key. Anyone who has a public key can
encrypt information but cannot decrypt it. Only the person who has the
corresponding private key can decrypt the information.
PUBLIC KEY INFRASTRUCTURE (PKI) AND
DIGITAL SIGNATURES
Public Key Infrastructure (PKI) refers to the technical mechanisms, procedures and
policies that collectively provide a framework for addressing the previously
illustrated fundamentals of security-authentication,
confidentiality, integrity, non-repudiation and access control.
PKI enables people and businesses to utilise a number of
secure Internet applications. For example, secure and legally binding emails
and Internet based transactions, and services delivery can all be achieved
through the use of PKI.
PKI utilises two core elements; Public Key Cryptography and Certification
Authorities.
The benefits of PKI are delivered through the use of Public Key
Cryptography. A core aspect of Public Key Cryptography is the encryption and
decryption of digital data.
A major benefit of public key
cryptography is that it provides a method for employing digital signatures.
Digital signatures enable the recipient of information to verify the
authenticity of the information’s origin, and also verify that the information
is intact. Thus, public key digital signatures provide authentication and data
integrity. A digital signature also provides non-repudiation, which means that
it prevents the sender from claiming that he or she did not actually send the
information. These features are every bit as fundamental to cryptography as
privacy, if not more.
A digital signature serves the
same purpose as a handwritten signature. However, a handwritten signature is
easy to counterfeit. A digital signature is superior to a handwritten signature
in that it is nearly impossible to counterfeit, plus it attests to the contents
of the information as well as to the identity of the signer.
The basic manner in which digital
signatures are created is illustrated in the figure given on the previous page.
Instead of encrypting information using someone else’s public key, you encrypt
it with your private key. If the information can be decrypted with your public
key, then it must have originated with you.
Digital Signatures apply the same functionality to an
e-mail message or data file that a handwritten signature does for a paper-based
document. The Digital Signature vouches for the origin and integrity of a
message, document or other data file.
The creation of a Digital Signature is a complex mathematical process.
However as the complexities of the process are computed by the computer,
applying a Digital Signature is no more difficult that creating a handwritten
one!
The following process illustrates in
general terms the processes behind the generation of a Digital Signature:
1.
Alice clicks
'sign' in her email application or selects which file is to be signed.
2.
Alice's
computer calculates the 'hash' (the message is applied to a publicly known mathematical
hashing function that coverts the message into a long number referred to as the
hash).
3.
The hash is
encrypted with Alice's Private Key (in this case it is known as the Signing
Key) to create the Digital Signature.
4.
The original
message and its Digital Signature are transmitted to Bob.
5.
Bob receives
the signed message. It is identified as being signed, so his email application
knows which actions need to be performed to verify it.
6.
Bob's
computer decrypts the Digital Signature using Alice's Public Key.
7.
Bob's
computer also calculates the hash of the original message (remember - the
mathematical function used by Alice to do this is publicly known).
8.
Bob's
computer compares the hashes it has computed from the received message with the
now decrypted hashes received with Alice's message.
Represented diagrammatically:
If the message has remained integral
during its transit (i.e. it has not been tampered with), when compared the two
hashes will be identical.
However, if the two hashes differ when
compared then the integrity of the original message has been compromised. If
the original message is tampered with it will result in Bob's computer
calculating a different hash value. If a different hash value is created, then
the original message will have been altered. As a result the verification of
the Digital Signature will fail and Bob will be informed.
DIGITAL
CERTIFICATE AND ITS TYPES
In a public key environment, it
is vital that you are assured that the public key to which you are encrypting
data is in fact the public key of the intended recipient and not a forgery. You
could simply encrypt only to those keys which have been physically handed to
you. But suppose you need to exchange information with people you have never
met; how can you tell that you have the correct key?
Digital
certificates,
or Certs,
simplify the task of establishing whether a public key truly belongs to the
purported owner.
A certificate is a form of
credential. Examples might be your driver’s license, your social security card,
or your birth certificate. Each of these has some information on it identifying
you and some authorization stating that someone else has confirmed your
identity. Some certificates, such as your passport, are important enough
confirmation of your identity that you would not want to lose them, lest
someone use them to impersonate you.
A digital certificate is data
that functions much like a physical certificate. A digital certificate is
information included with a person’s public key that helps others verify that a
key is genuine or valid. Digital certificates are used to thwart attempts to
substitute one person’s key for another.
A digital certificate consists of
three things:
§ A public key.
§ Certificate information (“Identity” information
about the user, such as name, user ID, and so on.)
§ One or more digital signatures.
In
other words, Alice's Digital Certificate attests to the fact that her Public
Key belongs to her, and only her. As well as the Public Key, a Digital
Certificate also contains personal or corporate information used to identify
the Certificate holder, and as Certificates are finite, a Certificate expiry
date.
Digital Certificates and Certification Authorities
Digital Certificates are issued by Certification
Authorities (CA). Like a central trusted body is used to issue driving licenses
or passports, a CA fulfils the role of the Trusted Third Party by accepting
Certificate applications from entities, authenticating applications, issuing
Certificates and maintaining status information about the Certificates issued. The
incorporation of a CA into PKI ensures that people cannot masquerade on the Internet
as people they are not by issuing their own fake Digital Certificates for
illegitimate use.
The Trusted Third Party CAs will
verify the identity of the Certificate applicant before attesting to their
identity by Digitally Signing the applicant's Certificate. Because the Digital
Certificate itself is now a signed data file, its authenticity can be
ascertained by verifying its Digital Signature. Therefore, in the same way we
verify the Digital Signature of a signed message, we can verify the
authenticity of a Digital Certificate by verifying its signature. Because CAs
are trusted, their own Public Keys used to verify the signatures of issued Digital
Certificates are publicised through many mediums widely.
The CA provides a Certification
Practice Statement (CPS) that clearly states its policies and practices
regarding the issuance and maintenance of Certificates within the PKI. The CPS contains operational information and legal
information on the roles and responsibilities of all entities involved in the
Certificate lifecycle (from the day it is issued to the day it expires). Digital
Certificates are issued under the technical recommendations of the x.509
Digital Certificate format as published by the International Telecommunication
Union-Telecommunications Standardization Sector (ITU-T).
Enrolling for
a Digital Certificate
Users may en-roll for a Digital
Certificate via the Web. Upon completion of the necessary forms, the user's
Internet Browser will create a Public Key Pair. The Public half of the key pair
is then sent to the CA along with all other data to appear in the Digital
Certificate, while the Private Key is secured on the user's chosen storage
medium (hard disk, floppy or hardware token, etc).
The CA must verify the submitted data
before binding the identification data to the submitted Public Key. This
prevents an impostor obtaining a Certificate that binds his Public Key to
someone else's identity and conducting fraudulent transactions using that
identity. If submitted data is in good order the CA will issue a Digital
Certificate to the applicant stated within the submitted information. Upon
issuance, the CA will enter the Digital Certificate into a public repository.
Distributing Digital Certificates:
As well as Digital Certificates being
available in public repositories, they may also be distributed through the use
of Digital Signatures. For example, when Alice Digitally signs a message for
Bob she also attaches her Certificate to the outgoing message. Therefore, upon
receiving the signed message Bob can verify the validity of Alice's
Certificate. If it is successfully verified, Bob now has Alice's Public Key and
can verify the validity of the original message signed by Alice.
Different types of Digital Certificate
Dependent on their usage Digital
Certificates are available in a number of different types:
▫
Personal: Used by
Individuals requiring secure email and web based transactions.
▫
Organisation: Used by
corporate to identify employees for secure email and web based transactions.
▫
Server: To
prove ownership of a domain name and establish SSL / TLS encrypted sessions
between their website and a visitor.
▫
Developer: To
prove authorship and retain integrity of distributed software programs.
Using
Digital Certificates to deliver the 5 primary security functions:
1.
Identification
/ Authentication: The CA attests
to the identity of the Certificate applicant when it signs the Digital
Certificate.
2.
Confidentiality: The Public Key within the Digital
Certificate is used to encrypt data to ensure that only the intended recipient
can decrypt and read it.
3.
Integrity: By Digitally Signing the message
or data, the recipient has a means of identifying any tampering made on the
signed message or data.
4.
Non-Repudiation: A signed message proves origin,
as only the sender has access to the Private Key used to sign the data.
5.
Access Control: Access Control may be achieved
through use of the Digital Certificate for identification (and hence the
replacement of passwords etc). Additionally, as data can be encrypted for
specific individuals, we can ensure that only the intended individuals gain
access to the information within the encrypted data.
FIREWALL: COMMON
FIREWALL TECHNIQUES AND PERSONAL FIREWALL
A firewall is a software program
or piece of hardware that helps screen out hackers, viruses, and worms that try
to reach your computer over the Internet.
A
firewall is a system designed to prevent unauthorized access to or from a
private network. Firewalls can be implemented in both hardware and software, or
a combination of both. Firewalls are frequently used to prevent unauthorized
Internet users from accessing private networks connected to the Internet,
especially intranets. All messages entering or leaving the intranet pass
through the firewall, which examines each message and blocks those that do not
meet the specified security criteria.
Common
Firewall Techniques
Firewalls are used to protect
both home and corporate networks. A typical firewall program or hardware device
filters all information coming through the Internet to your network or computer
system. There are several types of firewall techniques that will prevent
potentially harmful information from getting through:
§ Packet Filter
Looks at each
packet entering or leaving the network and accepts or rejects it based on
user-defined rules. Packet filtering is fairly effective and transparent to
users, but it is difficult to configure. In addition, it is susceptible to IP
spoofing.
§ Application Gateway
Applies security
mechanisms to specific applications such as FTP (File Transfer Protocol) and
Telnet servers. This is very effective but can impose performance degradation.
§ Circuit-level Gateway
Applies security
mechanisms when a TCP or UDP connection is established. Once the connection has
been made, packets can flow between the hosts without further checking.
§ Proxy Server
Intercepts all
messages entering and leaving the network. The proxy server effectively hides
the true network addresses.
In practice, many firewalls use
two or more of these techniques in concert. A firewall is considered a first
line of defence in protecting private information. For greater security, data
can be encrypted.
PERSONAL
FIREWALL
A personal firewall is the
software installed in a user's computer that offers protection against unwanted
intrusion and attacks coming from the Internet.
A personal firewall (sometimes
called a desktop firewall) is a software application used to protect a single
Internet-connected computer from intruders. Personal firewall protection is
especially useful for users with "always-on" connections such as DSL* (Digital Subscriber Line) or cable modem. Such connections use a
static IP address that makes them especially vulnerable to potential hackers.
Often compared to anti-virus applications, personal firewalls work in the
background at the device (link layer) level to protect the integrity of the
system from malicious computer code by controlling Internet connections to and
from a user's computer, filtering inbound and outbound traffic, and alerting
the user to attempted intrusions.
It is an application which
controls network traffic to and from a computer, permitting or denying
communications based on a security policy. Typically it works as an application
layer firewall.
A personal firewall differs from
a conventional firewall in terms of scale. A personal firewall will usually
protect only the computer on which it is installed, as compared to a
conventional firewall which is normally installed on a designated interface
between two or more networks, such as a router or proxy server. Hence, personal
firewalls allow a security policy to be defined for individual computers,
whereas a conventional firewall controls the policy between the networks that
it connects.
The per-computer scope of
personal firewalls is useful to protect machines that are moved across
different networks. For example, a
laptop computer may be used on a trusted intranet at a workplace where minimal
protection is needed as a conventional firewall is already in place, and
services that require open ports such as file and printer sharing are useful.
The same laptop could be used at public Wi-Fi hotspots, where strict security
is required to protect from malicious activity. Most personal firewalls will
prompt the user when a new network is connected for the first time to decide
the level of trust, and can set individual security policies for each network.
*DSL-It is a technology for bringing high-bandwidth
information to homes and small businesses over ordinary copper telephone lines.
Features
of a Personal Firewall
Common personal firewall
features:
▫ Protects the user from unwanted incoming connection
attempts
▫ Allows the user to control which programs can and
cannot access the local network and/or Internet and provide the user with
information about an application that makes a connection attempt
▫ Block or alert the user about outgoing connection
attempts
▫ Hide the computer from port scans by not responding
to unsolicited network traffic
▫ Monitor applications that are listening for incoming
connections
▫ Monitor and regulate all incoming and outgoing
Internet users
▫ Prevent unwanted network traffic from locally
installed applications
▫ Provide information about the destination server
with which an application is attempting to communicate
SECURITY
PROTOCOLS
The Hypertext Transfer Protocol (HTTP) is an
application-level protocol for distributed, collaborative, hypermedia
information systems. HTTP has been in use by the World-Wide Web global
information initiative since 1990. The first version of HTTP, referred to as
HTTP/0.9, was a simple protocol for raw data transfer across the Internet.
HTTP/1.0, as defined by RFC* 1945
[6], improved the protocol by allowing messages to be in the format of
MIME-like messages, containing meta-information about the data transferred and
modifiers on the request/response semantics. However, HTTP/1.0 does not
sufficiently take into consideration the effects of hierarchical proxies,
caching, the need for persistent connections, or virtual hosts. In addition,
the proliferation of incompletely-implemented applications known as
"HTTP/1.0" has necessitated a protocol version change in order for
two communicating applications to determine each other's true capabilities.
*Request for Comments-A
Request for Comments (RFC) is a formal document from the Internet Engineering Task Force (IETF) that is the result of committee
drafting and subsequent review by interested parties.
The HyperText Transfer Protocol
defines how messages are formatted and transmitted, and what actions Web
servers and browsers should take in response to various commands. For example,
when you enter a URL in your browser, this actually sends an HTTP command to
the Web server directing it to fetch and transmit the requested Web page.
HTTP is designed to permit
intermediate network elements to improve or enable communications between
clients and servers. HTTP functions as a request-response protocol in the
client-server computing model. A web browser, for example, may be the client
and an application running on a computer hosting a web site may be the server.
The client submits an HTTP request message to the server. The server which
provides resources, such as HTML files and other content, or performs other
functions on behalf of the client returns a response message to the client. The
response contains completion status information about the request and may also
contain requested content in its message body.
The other main standard that
controls how the World Wide Web works is HTML
(HyperText Markup Language: it is the main markup language for creating
web pages and other information that can be displayed in a web browser),
which covers how Web pages are formatted and displayed.
HTTP is called a stateless protocol because each
command is executed independently, without any knowledge of the commands that
came before it. This is the main reason that it is difficult to implement Web
sites that react intelligently to user input. This shortcoming of HTTP is being
addressed in a number of new technologies, including ActiveX, Java, JavaScript
and cookies.
The Secure Socket Layer (SSL)
and Transport Layer Security (TLS) is the most widely deployed security
protocol used today. It is essentially a protocol that provides a secure
channel between two machines operating over the Internet or an internal
network. In today’s Internet focused world, the SSL protocol is typically used
when a web browser needs to securely connect to a web server over the
inherently insecure Internet.
Technically, SSL is a transparent
protocol which requires little interaction from the end user when establishing
a secure session. In the case of a browser for instance, users are alerted to
the presence of SSL when the browser displays a padlock, or, in the case of
Extended Validation SSL, when the address bar displays both a padlock and a
green bar. This is the key to the success of SSL – it is an incredibly simple
experience for end users.
Usage
of SSL, in practice, in today’s modern e-commerce enabled / online workflow and
service society:
§ To secure online credit card transactions.
§ To secure system logins and any sensitive
information exchanged online.
§ To secure webmail and applications like Outlook Web
Access, Exchange and Office Communications Server.
§ To secure workflow and virtualisation applications
like Citrix Delivery Platforms or cloud-based computing platforms.
§ To secure the connection between an email client
such as Microsoft Outlook and an email server such as Microsoft Exchange.
§ To secure the transfer of files over https and
FTP(s) services such as website owners updating new pages to their websites or
transferring large files.
§ To secure hosting control panel logins and activity
like Parallels, cPanel, and others.
§ To secure intranet based traffic such as internal
networks, file sharing, extranets, and database connections.
§ To secure network logins and other network traffic
with SSL VPNs such as VPN Access Servers or applications like the Citrix Access
Gateway.
All
these applications have a number of shared themes:
§ The data being transmitted over the Internet or
network needs confidentiality. In other words, people do not want their credit
card number, account login, passwords or personal information to be exposed
over the Internet.
§ The data needs to remain integral, which means that
once credit card details and the amount to be charged to the credit card have
been sent, a hacker sitting in the middle cannot change the amount to be
charged and where the funds should go.
§ Your organisation needs identity assurance to
authenticate itself to customers / extranet users and ensure them they are
dealing with the right organisation.
§ Your organisation needs to comply with regional,
national or international regulations on data privacy, security and integrity.
Standard
SSL Certificates (such as GlobalSign DomainSSL and OrganizationSSL) display:
Extended
Validation (EV) SSL Certificates (such as GlobalSign ExtendedSSL) display
visible trust indicators:
As opposed to unsecured HTTP URLs
which begin with "http://" and use port 80 by default, secure HTTPS
URLs begin with "https://" and use port 443 by default.
HTTP is insecure and is subject
to eavesdropping attacks which, if critical information like credit card
details and account logins is transmitted and picked up, can let attackers gain
access to online accounts and sensitive information. Ensuring data is either
sent or posted through the browser using HTTPS is ensuring that such
information is encrypted and secure.
INTRUSION
DETECTION SYSTEM (IDS) AND VIRTUAL PRIVATE NETWORK (VPN)
Intrusion
Detection System
(IDS) is a type of security
management system for computers and networks. An ID system gathers and analyzes
information from various areas within a computer or a network to identify
possible security breaches, which include both intrusions (attacks from outside
the organization) and misuse (attacks from within the organization). ID uses
vulnerability assessment (sometimes referred to as scanning), which is a
technology developed to assess the security of a computer system or network.
Typically,
an ID system follows a two-step process. The first procedures are host-based
and are considered the passive component, these include: inspection of the
system's configuration files to detect inadvisable settings; inspection of the
password files to detect inadvisable passwords; and inspection of other system
areas to detect policy violations. The second procedures are network-based and
are considered the active component: mechanisms are set in place to re-enact
known methods of attack and to record system responses.
Intrusion
detection functions include:
▫
Monitoring and analyzing both user and
system activities
▫ Analyzing system configurations and vulnerabilities
▫ Assessing system and file integrity
▫ Ability to recognize patterns typical of attacks
▫ Analysis of abnormal activity patterns
▫ Tracking user policy violations
An
intrusion detection system (IDS) inspects all inbound and outbound
network activity and identifies suspicious patterns that may indicate a network
or system attack from someone attempting to break into or compromise a system.
There are
several ways to categorize the IDS:
§ Misuse detection vs. Anomaly detection: In misuse detection, the IDS analyses the
information it gathers and compares it to large databases of attack signatures.
Essentially, the IDS look for a specific attack that has already been
documented. Like a virus detection system, misuse detection software is only as
good as the database of attack signatures that it uses to compare packets
against. In anomaly detection, the
system administrator defines the baseline, or normal, state of the network’s
traffic load, breakdown, protocol, and typical packet size. The anomaly detector
monitors network segments to compare their state to the normal baseline and
look for anomalies.
§ Network-based vs. Host-based systems: In a network-based system, or NIDS, the individual packets flowing
through a network are analyzed. The NIDS can detect malicious packets that are
designed to be overlooked by a firewall’s simplistic filtering rules. In a host-based system, the IDS examines at
the activity on each individual computer or host.
§ Passive system vs. Reactive system: In a passive system, the IDS detect a
potential security breach, log the information and signal an alert. In a reactive system, the IDS respond to the
suspicious activity by logging off a user or by reprogramming the firewall to
block network traffic from the suspected malicious source.
Though they both relate to
network security, the IDS differ from a firewall in that a firewall looks out
for intrusions in order to stop them from happening. The firewall limits the
access between networks in order to prevent intrusion and does not signal an
attack from inside the network. The IDS evaluates a suspected intrusion once it
has taken place and signals an alarm. The IDS also watches for attacks that
originate from within a system.
A
Virtual Private Network (VPN) is a network that uses a public
telecommunication infrastructure, such as the Internet, to provide remote
offices or individual users with secure access to their organization's network.
A virtual private network can be contrasted with an expensive system of owned
or leased lines that can only be used by one organization. The goal of a VPN is
to provide the organization with the same capabilities, but at a much lower
cost.
A
VPN works by using the shared public infrastructure while maintaining privacy
through security procedures and tunnelling protocols such as the Layer Two
Tunnelling Protocol (L2TP). In effect, the protocols, by encrypting data at the
sending end and decrypting it at the receiving end, send the data through a
"tunnel" that cannot be "entered" by data that is not properly
encrypted. An additional level of security involves encrypting not only the
data, but also the originating and receiving network addresses.
VPN
is a network that is constructed by using public wires — usually the Internet —
to connect to a private network, such as a company's internal network. There are a number of systems that enable you
to create networks using the Internet as the medium for transporting data.
These systems use encryption and other security mechanisms to ensure that only
authorized users can access the network and that the data cannot be
intercepted.
Consumer VPN
Services
Consumers
use a private VPN service, also known as a VPN tunnel, to protect their online
activity and identity. By using an anonymous VPN service, a user's Internet
traffic and data remain encrypted, which prevents eavesdroppers from sniffing
Internet activity. A VPN service is
especially useful when accessing public Wi-Fi hotspots because the public
wireless services might not be secure. In addition to public Wi-Fi security, a
private VPN service also provides consumers with uncensored Internet access and
can help prevent data theft and unblock websites.
Corporate VPN
Communications
Companies
and organizations will use a VPN to communicate confidentially over a public
network and to send voice, video or data. It is also an excellent option for
remote workers and organizations with global offices and partners to share data
in a private manner.
One
of the most common types of VPNs used by businesses is called a virtual private
dial-up network (VPDN). A VPDN is a user-to-LAN connection, where remote users
need to connect to the company LAN. Another type of VPN is commonly called a
site-to-site VPN. Here the company would invest in dedicated hardware to
connect multiple sites to their LAN though a public network, usually the
Internet.
Key terms to understanding virtual private networks:
§ VPN: A
network that is constructed by using public wires to connect nodes. For
example, there are a number of systems that enable you to create networks using
the Internet as the medium for transporting data.
§ VPDN: A network that
extends remote access to a private network using a shared infrastructure.
§ Tunnelling: It
is a technology that enables one network to send its data via another network's
connections. Tunnelling works by encapsulating a network protocol within
packets carried by the second network.
§ Split tunnelling: The process of allowing a remote VPN user to access a public network,
most commonly the Internet, at the same time that the user is allowed to access
resources on the VPN.
§ Encryption: The
translation of data into a secret code. Encryption is the most effective way to
achieve data security. To read an encrypted file, you must have access to a
secret key or password that enables you to decrypt it. There are two main types
of encryption: asymmetric encryption (also called public-key encryption) and
symmetric encryption.
THE
CONCEPT OF E-MONEY AND ELECTRONIC PAYMENT SYSTEM
Electronic money is money which
exists only in banking computer systems and is not held in any physical form.
In the United States, only a small fraction of the currency in circulation
exists in physical form. The need for physical currency has declined as more
and more citizens use electronic alternatives to physical currency.
E-money is electronic money which is exchanged
electronically over a technical device such as a computer or mobile phone.
ELECTRONIC
PAYMENT SYSTEMS (EPS)
The
definition of an electronic payment system is a way of paying for goods or
services electronically, instead of using cash or a check, in person or by
mail.
▫ An example of an electronic payment system is Pay
Pal.
▫ An example of an electronic payment system is the
use of a credit card.
Issues
of trust and acceptance play a more significant role in the e-commerce world
than in traditional businesses as far as payment systems are concerned.
Traditionally,
a customer sees a product, examines it, and then pays for it by cash, check, or
credit card. In the e-commerce world, in most cases the customer does not
actually see the concrete product at the time of transaction, and the method of
payment is performed electronically.
EPS
enables a customer to pay for the goods and services online by using integrated
hardware and software systems. The main objectives of EPS are to increase
efficiency, improve security, and enhance customer convenience and ease of use.
While
customers pay for goods/services by cash, check, or credit cards in
conventional businesses, online buyers may use one of the following EPS to pay
for products/services purchased online:
· Electronic funds transfer (EFT): EFT involves electronic transfer of money by
financial institutions.
· Payment cards: They contain stored financial value that can be
transferred from the customer's computer to the businessman's computer.
· Credit cards: They
are the most popular method used in EPSs and are used by charging against the
customer credit.
· Smart cards: They
include stored financial value and other important personal and financial
information used for online payments.
· Electronic money (e-money/e-cash): This is standard money converted into an
electronic format to pay for online purchases.
· Online payment: This can be used for monthly payment for Internet, phone bills, etc.
· Electronic wallets (e-wallets): They are similar to smart cards as they
include stored financial value for online payments.
· Micro-payment systems: They are similar to e-wallets in that they
include stored financial value for online payments; on the other hand, they are
used for small payments.
· Electronic gifts: They are one way of sending electronic currency or gift certificates
from one individual to another. The receiver can spend these gifts in their
favourite online stores provided they accept this type of currency.
TYPES
OF ELECTRONIC PAYMENT SYSTEMS
1.
Credit card payment is the
most common type of payment method, which account for 80 percent of online
payments in the US and 50 percent of online purchases outside the US. To use
the digital credit card payment systems on web, it has been extended the
functionality and security to validate authentic owner of the card. Verified by
visa is introduced by Visa.
2.
Digital wallets are quicker,
efficient and easy way to pay online. Unlike credit card, payers need not to
enter credit card information every time of purchase, instead payers can pay by
one or two mouse click. Amazon’s 1-Click Shopping is one of the best-fitted
examples. Digital Wallets offer the
storing of the buyers personal information and fills this in at checkout making
it un-necessary for the buyer to have to manually input this each time they
want to make a purchase.
3.
Micro payment is designed to
purchase less than US$ 10. In other words, Micro payment is designed for
payments under $10 that are generally too small for credit card payments. Accumulated balance digital payment
systems enable the user to make micropayments as well as purchases and the
debit balance it stored for future payment through credit card or phone bill. Accumulated
balance digital payment systems are used to make micropayment and purchases on
the web. The shoppers receive invoice through their convenient utility bills
such as telephone bill, electricity bill, internet bill etc. For example,
Payment One charges its customers to their monthly telephone bill. Digital
accumulating balance payment systems are more like utility bills. This system
allows users to make multiple purchases, which will be totalled up and billed for
at the end of a time period.
This
is ideal for micro-transactions heavy websites, where numerous cheap items are
purchased frequently. The micro-payment system uses a technology similar to the
digital wallet, where the customer transfers some money into the online stored
value system and uses it to pay for digital products.
Many
vendors are involved in micro-payment systems, as it can be used for
transactions by
▫ Banks
▫ Internet Service Providers (ISPs)
▫ Telecommunications
▫ Content providers
▫ Premium search engines
4.
Stored value payment systems
enable the user to make instant payments based on a stored digital balance like
PayPal. Stored value payment system
is instant online payment and the maximum amount of purchase depends on the
value stored in a digital account. The digital account relies on the amount
stored in customers’ bank, checking, credit card account etc. It’s kind of
online debit account; E-Account offers a prepaid debit account for online
purchases.
5.
Smart card is another type
of stored value system used for micropayment. It’s kind of electronic purse
stored digital money with necessary information. To pay online by smart card, a
digital card reader (a device that read the information in smart card) is
necessary to attach with shoppers computer. American Express’s Blue smart card
is one of the good examples.
6.
Digital cash or electronic cash or e-cash is used for micropayment or larger purchases. Digital cash
represents the electronic form of currency which is not same as conventional
currency in the market. Users use specific software for trading and transacting
this electronic currency with other e-cash user or retailer through Internet.
ECoin.net is an example of a digital cash service.
7.
Web-based peer-to-peer
payment system us becoming very popular and its growing. The vendors or
individual who does not have any facility to accept payment through credit card
payment or any other convenient method, they can use this peer-to-peer to
accept payment. For example, millions of eBay buyers and sellers are using
PayPal to pay and receive payment.
8.
Digital checking enables the
user to extend the functionality of their existing checking accounts for online
shopping and they are processed much faster than the conventional checking
systems. Digital checking payment systems extend traditional checking system so
they can be used for online payment. It is less expensive than credit card and
much faster than traditional paper based checking. For example, Western Union
Money Zap and e-Check.
9.
Electronic
billing
presentment and payment systems are used to pay routine monthly bills through
electronic fund transfer from bank account and credit card account. Transaction
occurs online. Electronic billing presentment and payment systems are used for
the payment of recurring bills. They offer viewing of the account transactions
and reminders of due dates as well as payment options through existing credit
card accounts or bank transfers.
SMART
CARDS AND STORED-VALUE CARDS
Smart Cards
A
smart card, typically a type of chip card, is a plastic card that contains an
embedded computer chip–either a memory or microprocessor type–that stores and
transacts data. This data is usually associated with either value, information,
or both and is stored and processed within the card's chip. The card data is
transacted via a reader that is part of a computing system. Systems that are
enhanced with smart cards are in use today throughout several key applications,
including healthcare, banking, entertainment, and transportation. All
applications can benefit from the added features and security that smart cards
provide. Markets that have been traditionally served by other machine readable
card technologies, such as barcode and magnetic stripe, are converting to smart
cards as the calculated return on investment is revisited by each card issuer
year after year.
Applications of
Smart Cards
First
introduced in Europe nearly three decades ago, smart cards debuted as a stored
value tool for payphones to reduce theft. People found new ways to use smart
cards and other chip-based cards as they advanced, including charge cards for
credit purchases and for record keeping in place of paper.
In
the U.S., consumers have been using chip cards for everything from visiting
libraries to buying groceries to attending movies, firmly integrating them into
our everyday lives. Several U.S. states have chip card programs in progress for
government applications ranging from the Department of Motor Vehicles to
Electronic Benefit Transfers (EBTs). Many industries have implemented the power
of smart cards in their products, such as the GSM digital cellular phones as
well as TV-satellite decoders.
Smart
cards improve the convenience and security of any transaction. They provide
tamper-proof storage of user and account identity. Smart card systems have
proven to be more reliable than other machine-readable cards, like magnetic
stripe and barcode, with many studies showing card read life and reader life
improvements demonstrating much lower cost of system maintenance. Smart cards
also provide vital components of system security for the exchange of data
throughout virtually any type of network. They protect against a full range of
security threats, from careless storage of user passwords to sophisticated
system hacks. The costs to manage password resets for an organization or
enterprise are very high, thus making smart cards a cost-effective solution in
these environments. Multifunction cards can also be used to manage network
system access and store value and other data. Worldwide, people are now using
smart cards for a wide variety of daily tasks
Stored Value
Cards
A
stored value card is like a universal gift card. It is issued in a given amount
of money, and it is not associated with any individual name or person. Instead,
this card can be used at any time in order to make a purchase; it is like cash.
With a prepaid card, the individual holding the card physically deposits money
into an account. The person's name is on the card and the magnetic strip on the
card accesses the account in this same person's name. A stored value card is
totally independent from any bank account, giving it unique benefits and risks.
Today,
there are Electronic Benefits Transfer (EBT) cards, gift cards, payroll cards
and even “teen” cards (usually purchased by a parent on behalf of a teenager).
Stored-value
cards can either be single purpose (closed loop) or multipurpose (open loop).
Single-purpose cards, such as store and EBT cards, are good only at a specific
retailer or group of retailers — hence the phrase “closed loop.” In a closed-loop transaction, a nonbank service
provider issues cards on behalf of its customer. When consumers use these cards
to purchase goods, the service provider authorizes the transaction against a
proprietary database and debits the “prefunded” account for the amount of the
transaction. In essence, the transaction stays on the store’s books.
FIs
typically offer the multipurpose variety of stored-value cards, including gift
cards, teen cards and payroll cards. These types of cards are issued with card
association branding, such as Visa®, MasterCard® and Discover®. Therefore, they
are accepted anywhere the association brand is accepted, making them “open loop”.
Benefits to
Financial Institutions
From
a financial institution’s (FI) perspective, offering stored-value cards helps
attract new customers and provide an alternative acquisition tool for those
that do not qualify for traditional credit or debit card products. In addition,
it enables FIs to create a new stream of incremental and recurring revenue from
usage and interchange fees generated from transactions.
Advantages of
using a stored-value card
Use in
"Credit Card Only" Scenarios: For
an individual without a credit card, it can be very challenging to complete
certain purchases. For example, credit cards are required to book plane tickets
and hotel rooms and to make other reservations. Some retailers have even begun to
operate on a "plastic only" basis. If you find yourself in one of
these scenarios, having a stored value card can save you from failure to make a
payment. The card has a magnetic strip and a credit card number. Either can be
used to make your purchase.
Control Costs
and Expenses:
You may find a situation where you need
to control your costs and expenses with a firmer hand than usual. For example,
you may be travelling or giving a credit card to your children or employees. In
this type of situation, having control over just how much can be spent is
important. You can purchase a stored value card in nearly any grocery store or
convenience store today. Once you do, you no longer have to worry about
carrying cash, overcharging on your credit card or giving into unnecessary
expenses. Your card will work only until you have spent all of the stored
value.
Disadvantages of
using a stored-value card
High Fees: The card you purchase costs money. For
example, a `200 stored value card may cost `220. The additional `20 goes to pay
for the physical card, the packaging, and the fees associated with the card's
usage. Ultimately, if you compare using a stored value card to using cash on
each purchase, you will find you spend more money by using the stored value
card. For example, if you want to give your child a gift, you may think `100 is
appropriate. You could give him or her `100 in cash, or you could provide a `90
stored value card.
"Like
Cash":
Since the card is not associated with any
individual name or account, it is like cash. You can spend it anywhere cards
are accepted without unique charges and fees. However, on the flip side, if you
lose the card, you cannot retain its value. The card is not associated with you
or your bank account. Any person who picks up the card can use it for a
purchase. The cashier accepting the card will not even ask for identification.
You cannot call the card issuer to have the card replaced. You have simply lost
the money.
INFRASTRUCTURE
ISSUES IN USING ELECTRONIC PAYMENT SYSTEM
Infrastructure
is necessary for the successful implementation of electronic payments. Proper
infrastructure for electronic payments is a challenge.
1.
For electronic
payments to be successful there is the need to have reliable and cost effective infrastructure that can be accessed by
majority of the population.
2.
Electronic
payments communication infrastructure includes computer network such as the
internet and mobile network used for mobile phone.
3.
In addition, banking activities and operations need to be automated. A network
that links banks and other financial institutions for clearing and payment
confirmation is a pre-requisite for electronic payment systems. Mobile network
and Internet are readily available in the developed world and users usually do
not have problems with communication infrastructure.
4.
Good communication Infrastructure: “Poor communication infrastructure
(Internet and mobile networking) is one of the reasons that hinder the
e-payment system”. Low level of internet
penetration and poorly developed telecommunication infrastructure impede smooth
development and improvements in e-commerce. Efforts by the government and other
financial and ICT (Information and
Communications Technology) stakeholders to move country’s payment system from a
cash-dependent platform to the globally acceptable electronic-driven
alternative may be impeded by dearth of critical telecommunication
infrastructure.
5.
In developing
countries, many of the rural areas are unbanked and lack access to critical infrastructure that drives electronic
payments.
6.
Some of the debit cards technologies like Automated
Teller Machines (ATMs) are still seen by many as unreliable for financial
transactions as stories told by people suggested that they could lose their
money through fraudulent deductions, debits and other lapses for which the
technology had been associated with by many over the last few years.
7.
Telecommunication and electricity are not available throughout the country, which
negatively affect the development of e-payments. The development of information
and communication technology is a major challenge for e-payments development.
Since ICT is in its infant stages in Nepal, the country faces difficulty
promoting e-payment development.
8.
Regulatory and Legal issues: National, regional or international set of laws,
rules and other regulations are important requirements for the successful
implementation of e-payment schemes. Some of the major elements include rules
on money laundering, supervision of commercial banks and e-money institutions
by supervisory authorities, payment system oversight by central banks, consumer
and data protection, cooperation and competition issues. The virtual and global
nature of e-payment also raises legal questions such as which jurisdiction will
be competent and about applicable laws in disputed cases, validity of
electronic, electronic contracts and electronic signature. A legal and
regulatory framework that builds trust and confidence supporting technical
efforts is an important issue to be addressed in implementing e-payments.
ELECTRONIC
FUND TRANSFER
An
Electronic Funds Transfer (EFT) is a
transaction that takes place over a computerized network, either among accounts
at the same bank or to different accounts at separate financial institutions.
Today,
electronic funds transfer allows you to exchange funds between individuals as
well as organizations via electronic gateways which can be accessed using
internet, computers and smart phones. Funds can be transferred instantly from
one account to another, either within the same bank or to a different bank
network at any given time.
Electronic
funds transfer is a much more preferred money transfer options it allows
customers to make money transfers at the comfort of their homes using
integrated banking tools such as internet and mobile banking.
Besides
being convenient, electronic transfer modes are considered to be safe, secure
and make transferring money much simpler. Electronic transfers are processed
immediately with the transferred amount being deducted from one account and
credited to the other in real time, thus saving time and effort involved in
physically transferring a sum of money. Opting for electronic transferring
system also reduces the possibilities of any mistakes as a transaction is only
authorized with complete details which include the correct account number of
the beneficiary and the target bank’s specific IFSC code.
EFT is one of the oldest electronic payment
systems. EFT is the groundwork of the cash-less and check-less culture where
and paper bills, checks, envelopes, stamps are eliminated. EFT is used for
transferring money from one bank account directly to another without any paper
money changing hands. The most popular application of EFT is that instead of
getting a pay-check and putting it into a bank account, the money is deposited
to an account electronically.
EFT
is considered to be a safe, reliable, and convenient way to conduct business.
The advantages of EFT contain the following:
· Simplified accounting
· Improved efficiency
· Reduced administrative costs
· Improved security
Today,
many users make payments electronically rather than in person. Hundreds of
electronic payment systems have been developed to provide secure Internet
transactions. Electronic payment systems are generally classified into four categories:
credit card and debit cards; electronic cash; micropayment systems; and
session-level protocols for secure communications.
A
secure electronic financial transaction has to meet the following four
requirements:
1)
Ensure that
communications are private;
2)
Verify that the
communications have not been changed in transmission;
3)
Ensure that the
client and server are who each claims to be; and
4)
Ensure that the
data to be transferred was, in fact, generated by the signed author.
Transferring
funds via electronic gateway is much simpler than the conventional methods. You
can choose to:-
§ Transfer funds into your own linked accounts of the
same bank network.
§ Transfer funds into different account of the same
bank.
§ Transfer funds into different bank’s accounts using
NEFT.
§ Transfer funds into other bank accounts using RTGS
§ Transfer funds into various accounts using IMPS.
Types of
electronic funds transfer
§ NEFT or National Electronics Funds Transfer
§ RTGS or Real Time Gross Settlement
§ IMPS or Immediate Payment Service
NEFT
The
National Electronic Funds Transfer is a nation-wide money transfer system which
allows customers with the facility to electronically transfer funds from their
respective bank accounts to any other account of the same bank or of any other
bank network. Not just individuals but also firms and corporate organizations
may use the NEFT system to transfer funds to and fro.
Funds
transfer through NEFT requires a transferring bank and a destination bank. With
the RBI organizing the records of all the bank branches at a centralized
database, almost all the banks are enabled to carry out an NEFT transaction.
Before transferring funds via NEFT you register the beneficiary, receiving
funds. For this you must possess information such as name of the recipient,
recipient’s bank name, a valid account number belonging to the recipient and
his respective bank’s IFSC code. These fields are mandatory for a funds
transfer to be authorized and processed. NEFT transactions can be ordered anytime
you want, even on holidays except for Sundays which are designated bank
holidays. However, the transactions are settled in batches defined by the
Reserve Bank of India depending upon specific time slots. There are 12
settlement batches operating at present between the time slot of 8 a.m. to 7
p.m. on weekdays and from 8 a.m. to 1 p.m. on Saturdays with 6 settlement
batches.
RTGS
Real
Time Gross Settlement as the name suggests is a real time funds transfer system
which facilitates you to transfer funds from one bank to another in real time
or on a gross basis. The transaction isn’t put on a waiting list and cleared
out instantly. RTGS payment gateway, maintained by the Reserve Bank of India
makes transactions between banks electronically. The transferred amount is
instantly deducted from the account of one banks and credited to the other
bank’s account.
Users
such as individuals, companies or firms can transfer large sums using the RTGS
system. The minimum value that can be transferred using RTGS is `2 Lakhs and
above. However there is no upper cap on the amount that can be transacted. The
remitting customer needs to add the beneficiary and his bank account details
prior to transacting funds via RTGS. A beneficiary can be registered through
your internet banking portal. The details required while transferring funds
would be the beneficiary’s name; his/her account number, receiver’s bank
address and the IFSC code of the respective bank.
On
successful transfer the Reserve Bank of India acknowledges the receiver bank
and based on this the both the remitting bank as well as the receiving bank
may/ may not notify the customers.
IMPS
Majority
of the funds transferred using electronic channels are processed via NEFT or
RTGS. But as the funds could only be cleared in batches using these transfer
gateways, the National Payments Corporation of India introduced a pilot mobile
payment project also known as the Immediate Payment Service (IMPS). Available
to Indian public, IMPS offers instant electronic transfer service using mobile
phones. IMPS interbank transfer service is available 24X7 and allows you to use
your mobile phones to access your account and to authorize transfer of funds
between accounts and banks. The IMPS service also features a secure transfer
gateway and an immediate confirmation on fulfilled orders.
IMPS
are offered on all the cellular devices via Mobile Banking or through SMS
facility. To be able to transfer money via IMPS route you must first register
for the immediate payment services with your bank. On obtaining the Mobile
Money Identifier (MMID) and MPIN from the bank you can login or make a request
via SMS to transfer a certain amount to a beneficiary. Meanwhile the
beneficiary must link his/her mobile number with his/her respective account and
obtain the MMID from the bank to be able to receive money.
To
initiate a transfer you must enter the beneficiary’s mobile number, beneficiary
MMID, the transfer amount and your MPIN while requesting the fund transfer. As
soon as the transaction is cleared, you receive a confirmation SMS on deduction
from your account and the money credited into the beneficiary’s account. The
transaction reference number can be noted for future reference.
Thus
IMPS enables customers to use mobile instruments as an instant money transfer
gateway, facilitating user convenience and saving time and effort involved in
other modes of transfer.
Difference
between NEFT, RTGS and IMPS
There is no cap on the minimum
value that can be transacted via NEFT. RTGS system however only process transactions
of a value starting from `2 Lakhs and above as it caters to gross settlements.
While the NEFT system settles transactions in batches, RTGS option transfer
funds in real time. Using NEFT if a transfer order is received after the
defined cut-off time, the transaction will have to wait until the next
clearance to be fulfilled whereas RTGS transactions are processed continuously
throughout the RTGS business hours. IMPS stands out as the most convenient and
instant mode of money transfer, allowing transfer of money across various
accounts and banks on the go using a mobile device.
BUSINESS TO
CONSUMER MODEL AND ITS TYPES
Business-to-consumer (B2C) is an
Internet and electronic commerce (e-commerce) model that denotes a financial
transaction or online sale between a business and consumer. B2C involves a
service or product exchange from a business to a consumer, whereby merchants
sell products to consumers. B2C is also known as business-to-customer (B2C).
Business-to-consumer (B2C) is
business or transactions conducted directly between a company and consumers who
are the end-users of its products or services.
While most companies that sell
directly to consumers can be referred to as B2C companies, the term became
immensely popular during the dotcom boom of the late 1990s, when it was used
mainly to refer to online retailers, as well as other companies that sold
products and services to consumers through the Internet.
Portal
Portals such as Yahoo,
MSN/Windows Live, and AOL offer users powerful Web search tools as well as an
integrated package of content and services, such as news, e-mail, instant
messaging, calendars, shopping, music downloads, video streaming, and more, all
in one place. Initially, portals sought to be viewed as “gateways” to the
Internet. Today, however, the portal business model is to be a destination
site. They are marketed as places where consumers will want to start their Web
searching and hopefully stay a long time to read news, find entertainment, and
meet other people.
E-Tailer
Online retail stores, often
called e-tailers, come in all sizes, from giant Amazon to tiny local stores
that have Web sites. E-tailers are similar to the typical bricks-and-mortar
storefront, except that customers only have to connect to the Internet to check
their inventory and place an order. Some e-tailers, which are referred to as
“bricks-and-clicks,” are subsidiaries or divisions of existing physical stores
and carry the same products. JCPenney, Barnes & Noble, Wal-Mart, and
Staples are four examples of companies with complementary online stores.
Others, however, operate only in the virtual world, without any ties to
physical locations. Amazon, BlueNile.com, and Drugstore.com are examples of
this type of e-tailer.
Content
Provider
Although there are many different
ways the Internet can be useful, “information content,” which can be defined
broadly to include all forms of intellectual property, is one of the largest
types of Internet usage. Intellectual property refers to all forms of human
expression that can be put into a tangible medium such as text, CDs, or the
Web. Content providers distribute information content, such as digital video,
music, photos, text, and artwork, over the Web. Content providers make money by
charging a subscription fee. For instance, in the case of Real.com’s Rhapsody Unlimited service, a monthly subscription fee
provides users with access to thousands of song tracks. Other content
providers, such as WSJ.com (The Wall Street Journal’s online newspaper),
Harvard Business Review, and many others, charge customers for content
downloads in addition to or in place of a subscription fee.
Transaction
Broker
Sites that process transactions
for consumers normally handled in person, by phone, or by mail are transaction
brokers. The largest industries using this model are financial services, travel
services, and job placement services. The online transaction broker’s primary
value propositions are savings of money and time. In addition, most transaction
brokers provide timely information and opinions. Sites, such as ‘Monster.com’ offer job searchers a
national marketplace for their talents and employers a national resource for
that talent. Both employers and job seekers are attracted by the convenience
and currency of information.
BUSINESS TO BUSINESS
MODEL AND ITS TYPES
Business to business refers to
business that is conducted between companies, rather than between a company and
individual consumers. This is in contrast to business to consumer (B2C) and
business to government (B2G).
Business to business (B2B) is a
type of commerce transaction that exists between businesses, such as those
involving a manufacturer and wholesaler, or a wholesaler and a retailer.
An example that illustrates the
business to business concept is automobile manufacturing. Many of a vehicle's
components are manufactured independently and the auto manufacturer must
purchase these parts separately. For instance, the tires, batteries,
electronics, hoses and door locks may be manufactured elsewhere and sold
directly to the automobile manufacturer.
There are many different types of
e-marketplace based on a range of business models. They can be broadly divided
into categories based on the way in which they are operated.
Independent
e-marketplace
An independent e-marketplace is
usually a business-to-business online platform operated by a third party which
is open to buyers or sellers in a particular industry. By registering on an
independent e-marketplace, you can access classified ads or requests for
quotations or bids in your industry sector. There will typically be some form
of payment required to participate.
For example, Hitachi, IBM, LG
Electronics, Matsushita Electric (Panasonic), Nortel Networks, Seagate
Technology, Solectron, and Toshiba, along with technology partners Ariba and
i2, announced the creation of e2open.com, an independent, global
business-to-business e-marketplace for the computer, electronics and
telecommunications industries. The new e-marketplace will run on technology
provided by Ariba, IBM and i2.
Buyer-oriented
e-marketplace
A buyer-oriented e-marketplace is
normally run by a consortium of buyers in order to establish an efficient
purchasing environment. If you are looking to purchase, participating in this
sort of e-marketplace can help you lower your administrative costs and achieve
the best price from suppliers. As a supplier you can use a buyer-oriented
e-marketplace to advertise your catalogue to a pool of relevant customers who
are looking to buy. For example, TimberWeb.com, www.citeulike.org
Supplier-oriented
e-marketplace
Also known as a supplier
directory, this marketplace is set up and operated by a number of suppliers who
are seeking to establish an efficient sales channel via the internet to a large
number of buyers. They are usually searchable by the product or service being
offered. Supplier directories benefit buyers by providing information about
suppliers for markets and regions they may not be familiar with. Sellers can
use these types of marketplace to increase their visibility to potential buyers
and to get leads.
For example, in the Yellow
Pages.com network alone in America, handles about 100 million business-related
searches per month. The internet is ubiquitous people can access it at home, at
school, wirelessly, and on their phones. The chances of having internet access
when you need to look up business listings are greater than having a phone book
around; this is why internet business directories can be so effective.
Vertical
and horizontal e-marketplaces
A vertical e-marketplace provides
online access to businesses vertically up and down every segment of a
particular industry sector such as automotive, chemical, construction or
textiles. Buying or selling using a vertical e-marketplace for your industry
sector can increase your operating efficiency and help to decrease supply chain
costs, inventories and procurement-cycle time.
A horizontal e-marketplace
connects buyers and sellers across different industries or regions. You can use
a horizontal e-marketplace to purchase indirect products such as office
equipment or stationery.
For example, W.W. Grainger, the
powerful MRO supplies group, provides a perfect example of the horizontal
trading community. Their exchange, OrderZone.com, went online in May 1999, and
provides a single Web portal that gives customers access to six
industry-leading MRO suppliers. The service includes online ordering and
invoicing and provides customers with a single point of contact for access to a
wide variety of indirect products. Only one registration on this single Web
site is necessary to gain access to not only Grainger.com and its MRO
catalogues, but to catalogues of other leading indirect suppliers for items
such as office and computer supplies, laboratory equipment, and uniforms.
BUSINESS TO GOVERNMENT, CONSUMER TO CONSUMER AND
CONSUMER TO BUSINESS MODELS
Business
to Government (B to G) Business Model
B2G are the professional affairs
conducted between companies and regional, municipal or federal governing
bodies. Business to government typically encompasses the determination and
evaluation of government agency needs, the creation and submission of proposals
and the completion of the contracted work.
On the Internet, B2G is
business-to-government (a variation of the term B2B or business-to-business),
the concept that businesses and government agencies can use central Web sites
to exchange information and do business with each other more efficiently than
they usually can off the Web. B2G may also support the idea of a virtual
workplace in which a business and an agency could coordinate the work on a
contracted project by sharing a common site to coordinate online meetings,
review plans, and manage progress. B2G may also include the rental of online
applications and databases designed especially for use by government agencies.
An example of a
business-to-government company is a firm that offers IT consulting services to
a government agency. The government uses the B2G arrangement in order to keep
its technology up to date and in working condition, while at the same time
limiting expenses by not taking on full-time staff who would require benefits.
Consumer
to Consumer (C to C) Business Model
It is a business model that
facilitates an environment where customers can trade with each other.
Consumer-to-consumer e-commerce
is the practice of individual consumers buying and selling goods via the
Internet. The most common type of this form of transaction comes via auction
sites, although online forums and classifieds also offer this type of commerce
to consumers. In most cases, consumer-to-consumer e-commerce, also known as C2C
e-commerce, is helped along by a third party, who officiates, the transaction
to make sure goods are received and payments are made. This offers some
protection for consumers partaking in C2C e-commerce, allowing them the chance
to take advantage of the prices offered by motivated sellers.
C2C or Consumer-to-consumer is a
business model where two individuals transact or conduct business with each
other directly. Generally an intermediary/third
party may be involved, but the purpose
of the intermediary is only to facilitate the transaction and provide a
platform for the people to connect. The intermediary would receive a fee or
commission, but is not responsible for the products exchanged. C2C normally
takes the form of an auction where the bidding is done online. Ebay.com and Amazon.com are the most notable sites performing such actions. C2C
reduces the cost with the similar interest consumers interact directly, thus
eliminating the need of a physical store. C2C can also take the form of virtual
communities where people who share the same interests interact with each other
and share ideas.
Auction websites, like the
extremely popular eBay, have recently sprung up all over the Internet and represent
the most popular form of consumer-to-consumer e-commerce. On an auction site,
one consumer will post the item or items for sale and then other users will bid
on the items. The user who comes up with the highest price in the allotted time
for the sale will receive the item in question.
Other sites exist that are
devoted to the process of consumer-to-consumer e-commerce. Online classified
sites work just like the typical classified ad in a newspaper. One user puts up
an ad describing the goods or services being offered and the desired price, and
other users seeking those goods or services can respond.
Consumer
to Business (C to B) Business Model
In C2B, the companies typically
pay for the product or service. However, it can assume different forms like an
idea generated by an individual (like an innovative business practice) which
may be used and implemented by an organization. Another possible form of C2B is
where a consumer specifies a need and the various businesses compete or bid to
fulfil that need.
Consumer-to-business (C2B) is a
business model in which consumers (individuals) create value, and firms consume
this value. For example, when a consumer writes reviews, or when a consumer
gives a useful idea for new product development, then this individual is
creating value to the firm, if the firm adopts the input. Another form of C2B
is the electronic commerce business model, in which consumers can offer
products and services to companies and the companies pay them. This business
model is a complete reversal of traditional business model where companies
offer goods and services to consumers (business-to-consumer = B2C). We can see
this example in blogs or internet forums where the author offers a link back to
an online business facilitating the purchase of some product (like a book on
Amazon.com), and the author might receive affiliate revenue from a successful
sale.
REVENUE MODELS
OF E-BUSINESS
A
firm’s revenue model describes how the firm will earn revenue, generate
profits, and produce a superior return on invested capital. We use the terms
revenue model and financial model interchangeably. The function of business
organizations is both to generate profits and to produce returns on invested
capital that exceed alternative investments. Profits alone are not sufficient
to make a company “successful” (Porter, 1985). In order to be considered
successful, a firm must produce returns greater than alternative investments.
Firms that fail this test go out of existence.
Retailers,
for example, sell a product, such as a personal computer, to a customer who
pays for the computer using cash or a credit card. This produces revenue. The
merchant typically charges more for the computer than it pays out in operating
expenses, producing a profit. But in order to go into business, the computer
merchant had to invest capital—either by borrowing or by dipping into personal
savings. The profits from the business constitute the return on invested
capital, and these returns must be greater than the merchant could obtain
elsewhere, say, by investing in real estate or just putting the money into a
savings account.
Although
there are many different e-commerce revenue models that have been developed,
most companies rely on one, or some combination, of the following major revenue
models: the advertising model, the
subscription model, the transaction fee model, the sales model, and the
affiliate model.
In
the Advertising Revenue Model, a Web site that offers its users content,
services, and/or products also provides a forum for advertisements and receives
fees from advertisers. Those Web sites that are able to attract the
greatest viewership or that have a highly specialized, differentiated
viewership and are able to retain user attention (“stickiness”) are able to
charge higher advertising rates. Yahoo, for instance, derives a
significant amount of revenue from search engine and other forms of online
advertising.
In
the Subscription Revenue Model, a Web site that offers its users content or
services charges a subscription fee for access to some or all of its offerings.
For instance, the online version of Consumer Reports provides access to
premium content, such as detailed ratings, reviews and recommendations, only to
subscribers, who have a choice of paying a $5.95 monthly subscription fee or a
$26.00 annual fee. Experience with the subscription revenue model indicates
that to successfully overcome the disinclination of users to pay for content on
the Web, the content offered must be perceived as a high-value-added, premium
offering that is not readily available elsewhere nor easily replicated.
Companies successfully offering content or services online on a subscription
basis include Match.com and eHarmony (dating services), Ancestry.com
and Genealogy.com
(genealogy research), Microsoft's Xboxlive.com (video
games), Rhapsody Online (music), among others.
In
the Transaction Fee Revenue Model, a company receives a fee for enabling or
executing a transaction. For example, eBay provides an online auction
marketplace and receives a small transaction fee from a seller if the seller is
successful in selling the item. E*Trade, an online stockbroker,
receives transaction fees each time it executes a stock transaction on behalf
of a customer.
In
the Sales Revenue Model, companies derive revenue by selling goods,
information, or services to customers. Companies such as Amazon
(which sells books, music, and other products), LLBean.com, and Gap.com,
all have sales revenue models.
In
the Affiliate Revenue Model, sites that steer business to an “affiliate”
receive a referral fee or percentage of the revenue from any resulting sales.
For example, MyPoints makes money by connecting companies with potential
customers by offering special deals to its members. When they take advantage of
an offer and make a purchase, members earn “points” they can redeem for
freebies, and MyPoints receives a fee. Community feedback sites such as Epinions
receive much of their revenue from steering potential customers to Web sites
where they make a purchase.
MOBILE COMMERCE
“M-commerce (mobile commerce) is the buying and selling of goods and
services through wireless handheld devices such as cellular telephone and personal
digital assistants (PDAs). Known as next-generation e-commerce, m-commerce
enables users to access the Internet without needing to find a place to plug
in. The emerging technology behind m-commerce, which is based on the Wireless
Application Protocol (WAP), has made far greater strides in Europe, where
mobile devices equipped with Web-ready micro-browsers are much more common than
in the United States.”
"Mobile Commerce is the use of information technologies and
communication technologies for the purpose of mobile integration of different
value chains an business processes, and for the purpose of management of
business relationships.“
“Mobile
Commerce is the use of wireless handheld devices such as cellular phones and
laptops to conduct commercial transactions online. Mobile commerce transactions
continue to grow, and the term includes the purchase and sale of a wide range
of goods and services, online banking, bill payment, information delivery and
so on.”
“The
term ‘m-commerce’ stands for mobile
commerce, and it’s the browsing, buying and selling of products and services on
mobile devices. In other words, it’s a complete online shopping experience, but
with all the convenience of being on a cell phone or tablet.”
As content delivery over wireless devices
becomes faster, more secure, and scalable, there is wide speculation that
m-commerce will surpass wire-line e-commerce as the method of choice for
digital commerce transactions. The industries affected by m-commerce include:
▫ Financial services, which includes mobile banking (when customers use their handheld
devices to access their accounts and pay their bills) as well as brokerage
services, in which stock quotes can be displayed and trading conducted from the
same handheld device.
▫ Telecommunications, in which service changes, bill payment and account reviews can all be
conducted from the same handheld device.
▫ Service/retail, as consumers are given the ability to place and pay for orders
on-the-fly.
▫ Information services, which include the delivery of financial
news, sports figures and traffic updates to a single mobile device.
IBM and other companies are
experimenting with speech recognition software as a way to ensure security for
m-commerce transactions.
The range of devices that are enabled
for mobile commerce is growing, having expanded in recent years to include
smart phones and tablet computers. The increasing adoption of electronic
commerce provided a strong foundation for mobile commerce, which is on a very
strong growth trajectory for years to come.
Mobile Commerce, or m-Commerce, is about
the explosion of applications and services that are becoming accessible from
Internet-enabled mobile devices. It involves new technologies, services and
business models. It is quite different from traditional e-Commerce. Mobile
phones impose very different constraints than desktop computers. But they also
open the door to a slew of new applications and services. They follow you
wherever you go, making it possible to look for a nearby restaurant, stay in
touch with colleagues, or pay for items at a store.
As the Internet finds its way
into our purses or shirt pockets, the devices we use to access it are becoming
more personal too. Already today, mobile phones know the phone numbers of our
friends and colleagues. They are starting to track our location. Tomorrow, they
will replace our wallets and credit cards. One day, they may very well turn
into intelligent assistants capable of anticipating many of our wishes and
needs, such as automatically arranging for taxis to come and pick us up after
business meetings or providing us with summaries of relevant news and messages
left by colleagues. But, for all these changes to happen, key issues of
interoperability, usability, security, and privacy still need to be addressed.
ETHICAL, LEGAL AND SOCIETAL
IMPACTS OF E-COMMERCE
E-Commerce has
the ability to provide secure shopping transactions coupled with instant
verification and validation of credit card transactions. E-Commerce is not
about the technology itself, it is about doing business leveraging the
technology. A technological innovation is followed by frequent incorporation of
ethical standards into law. New forms of E-Commerce that enables new business
practices have many advantages but also bring numerous risks. Let’s discuss about the ethical, legal and
societal issues related to e-business.
ETHICAL ISSUES
In general, many
ethical and global issues of Information Technology apply to e-business. Let’s
list some of the ethical issues initiated with the growing field of e-commerce.
Web tracking: E-businesses draw
information on how visitors use a site through log files. Analysis of log file
means turning log data into application service or installing software that can
pluck relevant information from files in-house. Companies track individual’s
movement through tracking software and cookie analysis. Programs such as
cookies raise a batch of privacy concerns. The tracking history is stored on
your PC’s hard disk, and any time you revisit a website, the computer knows it.
Many smart end users install programs such as Cookie cutters, Spam Butcher, etc
which can provide users some control over the cookies. The battle between
computer end users and web trackers is always going on with a range of
application programs. For example,
software such as Privacy Guardian, My Privacy, etc can protect user’s online
privacy by erasing browser’s cache, surfing history and cookies. To detect and remove spyware specially
designed programs like Ad-Aware are present. A data miner application, SahAgent
collects and combines Internet browsing history of users and sends it to
servers.
Privacy: Most Electronic Payment Systems
knows the identity of the buyer. So it is necessary to protect the identity of
a buyer who uses Electronic Payment System. A privacy issue related to the
employees of company is tracking. Monitoring systems are installed in many
companies to monitor e-mail and other web activities in order to identify
employees who extensively use business hours for non-business activities. The
e-commerce activities performed by a buyer can be tracked by organizations. For
example, reserving railway tickets for their personal journey purpose can be
tracked. Many employees don’t want to be under the monitoring system even while
at work. As far as brokers and some of
the company employees are concerned, E-Commerce puts them in danger zone and
results in elimination from their jobs.
The manner in which employees are treated may raise ethical issues, such
as how to handle displacement and whether to offer retraining programs.
Disintermediation and Re-intermediation:
Intermediation is one of the most important and interesting e-commerce issue
related to loss of jobs. The services provided by intermediaries are
(i)
Matching and providing information.
(ii)
Value added services such as consulting.
The first type
of service (matching and providing information) can be fully automated, and
this service is likely to be in e-marketplaces and portals that provide free
services. The value added service requires expertise and this can only be
partially automated. The phenomenon by
which Intermediaries, who provide mainly, matching and providing information,
services are eliminated is called Disintermediation. The brokers who provide
value added services or who manage electronic intermediation (also known as
info-mediation), are not only surviving but may actually prosper, this
phenomenon is called Re-intermediation. The traditional sales channel will be
negatively affected by disintermediation. The services required to support or
complement e-commerce are provided by the web as new opportunities for
re-intermediation. The factors that should be considered here are the enormous
number of participants, extensive information processing, delicate
negotiations, etc. They need a computer mediator to be more predictable.
LEGAL ISSUES
Internet fraud
and its sophistication have grown even faster than the Internet itself. There
is a chance of a crime over the internet when buyers and sellers do not know
each other and cannot even see each other. During the first few years of
e-commerce, the public witnessed many frauds committed over the internet. Let’s
discuss the legal issues specific to e-commerce.
Fraud on the Internet: E-commerce fraud
popped out with the rapid increase in popularity of websites. It is a hot issue
for both cyber and click-and-mortar merchants. The swindlers are active mainly
in the area of stocks. The small investors are lured by the promise of false
profits by the stock promoters. Auctions are also conductive to fraud, by both
sellers and buyers. The availability of e-mails and pop up ads has paved the
way for financial criminals to have access to many people. Other areas of
potential fraud include phantom business opportunities and bogus investments.
Copyright: The copyright laws
protect Intellectual property in its various forms, and cannot be used
freely. It is very difficult to protect
Intellectual property in E-Commerce. For example, if you buy software you have
the right to use it and not the right to distribute it. The distribution rights
are with the copyright holder. Also, copying contents from the website also
violates copy right laws.
Domain Names: The competition over
domain names is another legal issue. Internet addresses are known as domain
names and they appear in levels. A top level name is qburst.com or
microsoft.com. A second level name will be qburst.com/blog. Top level domain
names are assigned by a central non-profit organization which also checks for
conflicts or possible infringement of trademarks. Problems arise when several
companies having similar names competing over the same domain name. The problem of domain names was alleviated
somewhat in 2001 after several upper level names were added to com. Another
issue to look out for is Cyber-squatting,
which refers to the practice of registering domain names with the desire of
selling it at higher prices. Security features such as authentication,
non-repudiation and escrow services can protect the sellers in e-commerce.
One needs to be
careful while doing e-commerce activities. The need to educate the public about
the ethical and legal issues related to e-commerce is highly important from a
buyer as well as seller perspective.
Ecommerce allows
for items which may not be sold by outlets to be found online without having to
go from shop to shop, things such as distance also come into this as some
things may only be found in certain locations and thus by looking on the
internet for websites which sell these stuff you don’t have to travel to the destination
to get what you are looking for.
SOCIETAL ISSUES
Elimination of Distance: Ecommerce has
allowed companies to become more profitable because they don’t have to wait for
customers to come through the door to receive service, therefore putting their
products or services online, people could find this and buy the product or
service from them, things such as distance again apply in this.
Availability: Items can be brought
online on ecommerce as it allows products to be brought online at anytime
during the day or night as they don’t have times to work by. This also allows
for problems such as postage and items to be tracked when they are being sent
to a customer.
Cost-Saving: Ecommerce allows for
special offers because it gives different companies the chance to undercut each
other and to potentially make a lot of money because they don’t have the
overheads which a normal company has, such as hiring loads of staff to assist a
customer to buy extra things such as printing material or advertising banners
to hang up outside a store. Also ecommerce entities don’t need to buy or rent a
shop, thus cutting the cost right down because of this.
Phishing: Because ecommerce websites have
become popular many different websites are now mimicked as to get people to
falsely enter their details, websites are often phished and thus spring up
exact replicates of the original such as ASDA (ASDA Stores Ltd. is a British supermarket chain) being mimicked and
people enter their personal bank details. If this happens then a potential
customer may think it was ASDA who did this and therefore, if the customer is not
knowledgeable about security issues it may give ASDA or a different company a
bad name thus defaming a company and the original company may lose future
customers because of this issue.
Information Disclosure: Because
different people use ecommerce information is normally sold onto third-parties
such as customer address and phone number and other companies may try and force
a person to by a shop or item.
Hacking: Depending upon the authentication
methods of the website, the website may be subjected to ‘hacking’ techniques
for example if a authentication technique such as session authorisation is on,
then a attacker may change his/her session value and thus impersonate different
user on the website and dependent upon the website, he/she may be in legal trouble.
Health Issues: Ecommerce is so quick
now that people don’t want to be going out of their houses and because of this,
problems with things such as health may arise and thus people need to grasp
that they sometimes benefit from shopping around.
E-GOVERNANCE:
ITS PHASES AND BENEFITS
E-government refers to the delivery of national or local
government information and services via the Internet or other digital means to
citizens or businesses or other governmental agencies.
E-government is a one-stop Internet
gateway to major government services. E-government facilitates provision of
relevant government information in electronic form to the citizens in a timely
manner; better service delivery to citizens; empowerment of the people through
access to information without the bureaucracy; improved productivity and cost
savings in doing business with suppliers and customers of government; and
participation in public policy decision-making. E-Governance refers to how
managers and supervisors utilize IT and Internet to execute their functions of
supervising, planning, organizing, coordinating, and staffing effectively. The
emergence of Information and
Communications Technology (ICT) has provided means for faster and better
communication, efficient storage, retrieval and processing of data and exchange
and utilization of information to its users, be they individuals, groups,
businesses, organizations or governments.
According to the World Bank, “E-Government refers to the use by government agencies of information
technologies (such as Wide Area Networks, the Internet, and mobile computing)
that have the ability to transform relations with citizens, businesses, and
other arms of government. These technologies can serve a variety of different
ends: better delivery of government services to citizens, improved interactions
with business and industry, citizen empowerment through access to information,
or more efficient government management. The resulting benefits can be less
corruption, increased transparency, greater convenience, revenue growth, and/or
cost reductions.”
UNESCO defines
e-Governance as: “Governance refers to
the exercise of political, economic and administrative authority in the
management of a country’s affairs, including citizens’ articulation of their
interests and exercise of their legal rights and obligations. E-Governance may
be understood as the performance of this governance via the electronic medium
in order to facilitate an efficient, speedy and transparent process of
disseminating information to the public, and other agencies, and for performing
government administration activities.”
Gartner
Group’s
definition: “the continuous optimization
of service delivery, constituency participation, and governance by transforming
internal and external relationships through technology, the Internet and new
media.”
(Late)
Dr. APJ Abdul Kalam,
former President of India, had visualized e-Governance in the Indian context to
mean: “A transparent smart e-Governance
with seamless access, secure and authentic flow of information crossing the
interdepartmental barrier and providing a fair and unbiased service to the
citizen.”
Phases
of E-Governance: Gartner, an
international consultancy firm, has formulated four-phase e-governance
model. This can serve as a reference for governments to position where a
project fits in the overall evolution of an e-governance strategy.
Phase
I – Presence
This
first phase calls for making the intentions and objectives of the government
known. Development of an inclusive government website, or a network of sites
dedicated to different ministries and departments would set the stage for
further advancements. These sites would convey the government’s initiatives,
providing information such as official addresses, working hours, as well as forms
and applications to the public, economic reviews, corporate regulations for
business and budgetary allocations and spending as a reference for government
agencies.
Phase
II – Interaction
This
phase would allow for basic interaction with the government. Besides hosting
search engines on the sites for easy navigation, information detailing social
records and job application forms for the public, permit and license
documentation for businesses and census details, submission of requests and
approvals to the centre by local government officers would have to be provided.
Phase
III – Transaction
This
phase onwards would signify direct interaction of the government and relevant
entities. With the infrastructure in place, complete online service suites can
be put forth for the public, businesses and governmental agencies. Services for
the public such as bill and fine payments, license renewal, aggregating opinion
etc online procurement tax returns etc for businesses, cooperative budget
preparation, tax records, etc for governmental agencies can be envisaged here.
Phase
IV – Transformation
This final phase would strive to
achieve the true vision of e-Governance.
▫ A single point of contact to constituent entities
would provide an integrated platform for government services and organization
totally transparent to citizens and businesses.
▫ Focus on ‘virtual agencies’ where government
information is readily available to all allowing a seamless interface to
respective agencies involved in the transactions.
▫ State-of-the-art Intranets linking government
employees in different agencies extranets allowing seamless flow of information
thereby facilitating collaborative decisions among government agencies, NGO’s
and the public.
Types
of Interactions in e-Governance
▫ G2G (Government to Government) – In this case, Information and Communications
Technology is used not only to restructure the governmental processes involved
in the functioning of government entities but also to increase the flow of
information and services within and between different entities.
▫ G2C (Government to Citizens) – In this case, an interface is created
between the government and citizens which enables the citizens to benefit from
efficient delivery of a large range of public services.
▫ G2B (Government to Business) – Here, e-Governance tools are used to aid the
business community – providers of goods and services – to seamlessly interact
with the government.
▫ G2E (Government to Employees) – Government is by far the biggest employer
and like any organisation, it has to interact with its employees on a regular
basis. This interaction is a two-way process between the organisation and the
employee. Use of ICT tools helps in making these interactions fast and
efficient on the one hand and increase satisfaction levels of employees on the
other.
Benefits
of e-Governance
1.
Better access to
information and quality services for citizens:
ICT would make available timely and reliable information on various aspects of
governance.
2.
Simplicity,
efficiency and accountability in the government:
Application of ICT to governance combined with detailed business process
reengineering would lead to simplification of complicated processes, weeding
out of redundant processes, simplification in structures and changes in
statutes and regulations.
3.
Expanded reach
of governance: Rapid growth of
communications technology and its adoption in governance would help in bringing
government machinery to the doorsteps of the citizens.
EMERGING TRENDS IN E-BUSINESS
1.
Real-time
Shopping Experience at Online Shopping: There
is no doubt the people prefer to talk to real sales person and hold the product
in their hand! But do not think that e-commerce sites cannot offer you such
pleasure. Most online retailers have facilities to chat online, get suggestions
and answer all your queries. Online subscription even allow you to hold the
product and touch it (i.e. Stylemint, Birchbox), and some even lets you chat
all along while you are shopping with Chatalog.
2.
Less importance
to conversion ratio over customer engagements: Till date the conversion rates were given
the most priority but with the rise in e-commerce sites, gathering new
customers will be very tough. So naturally retailers will depend on holding on
to the existing customers. Customer engagement will ensure people develop a
liking for your site and follow you regularly. Currently conversion ratio
(visitors/orders) is of paramount importance. It sounds counter intuitive, but
this will reduce quite a lot over the coming period. Customer engagement and
making sure people have an emotional attachment with you and your product will
be the key. This means attracting consumers to the website with no intention of
buying on site, eventually driving more visitors on the site rather than
conversion ratio improvements. This eventually creates brand affinity and has
in turn positive impact on conversion and average order value (AOV) in other
channels.
3.
Personalization:
In an extremely volatile market one must
be ready for change all times- not otherwise but for personalization. Personalized
recommendations will find more prominence in the market. Although not new, it
will be more and more adopted as we go. Personalized recommendations or
targeted content will be the key medium to surface any content. There will be
two distinct sets of consumers; one who expects the retailer to make use of
cross domain data (i.e., if one has provided his data to Facebook or Twitter,
then he would expect it will be available to affiliates) and others who will be
wary of their data being shared between sites. Numbers-wise the former will be
higher than the latter.
4.
Social
Networking Sites:
As the social networking sites increase
in popularity, retailers must be using this platform for marketing and selling
their products! Facebook, Twitter, LinkedIn will be the platforms where you
will get data about the latest discounts and offers. Facebook has more than 850M+ subscribers, and it is a known fact
that number grows by 20% or more every year in emerging countries. Companies
will take more and more advantage from the various set of data about users’
daily activity using Facebook Connect, like offering promotions on products
which they most commented on or identifying what their friends mostly like and
recommending the same when they visit the store. Others like Pinterest, Groupon
and the likes are catching up slowly but with the existing user base, Facebook
will continue to lead the race. Social media sites increasingly act as points
of entry to e-commerce sites, and vice versa, as e-commerce sites build rating,
loyalty and referral systems tied to social media. Group buying (e.g., Groupon)
is also gaining mainstream ground, with many “deal of the day” sites competing
for an increasingly savvy consumer base, but improvements lie ahead as the
social aspects and user experience are refined.
5.
Mobile
technologies:
The potential growth of mobile/ iPad in retail
e-Commerce is enormous. With the current projections, in the next couple of
years mobile/ iPad will exceed desktop numbers. With the mobile devices
outnumbering the desktops, the use of these devices for buying will increase in
the near future. More people access the Internet on their mobile devices than
on any other device. We are rapidly approaching the time (if we are not already
there) where designs must be created for the mobile web first, and for the
desktop second. Mobile technologies facilitate comparison shopping; with the
advent of barcode reader apps and price-comparison databases, a consumer could
snap a bar code in Walmart and quickly reference product reviews and prices on
walmart.com (or compare prices with Walmart competitors). Mobile technologies also facilitate impulse
buys – especially with the advent of micro-payments tied to the mobile
device. Just recently, Starbucks
customers can not only place an order with their Smartphone, but also make a
purchase.
6.
Mobile POS and
Accessing via Mobile:
The idea of Mobile POS is to make each
and every employee work and allow the customer transact without being to the
billing counter. Thanks to the Android 4.2 Jellybean and iOS 6 that allows apps
that lets the customer do endless jobs with such apps. Apple started this trend
and most retailers do see significant advantage in this approach as you can not
only access the entire product range, but also drive assisted conversations.
With iOS 6 and Android 4.2 Jellybean, the features you can enable in the
customer assisted app are endless, starting from basic tools such as using the
camera for barcode scanning to doing a virtual makeover for customers in store.
7.
Push
notifications:
Current reactive nature of “pull
browsing” is changing very quickly to “push browsing”, whereby marketers are
reaching out to consumers with more relevancy than before to pull them to
buying things. What were earlier only marketing emails will turn into relevant
SMS notifications when a customer is standing outside the physical store or
relevant basket notifications when you are tweeting or Facebook updates for
selected products to your mobile home screen every morning. Pull browsing is
the latest trend now, but it is not far when push browsing will overtake it.
Messaging notifications, basket notifications for selective items on your home
page- are all going to catch up momentum.
8.
Multi-channel: Consumers will expect a seamless shopping
experience. They expect that a commodity added to the cart will be available if
one calls the customer care or land up in the store. In other words a product
added in a basket at home is expected to be found in the basket when you go to
the store or if you call up the call centre. This will drive investment by IT
directors in commerce packages, CRM systems and more importantly integrating
commerce system with POS.
9.
Big data: Big Data or Hadoop methodology is handling a
lot of data. This has been a concept that has been drawing the interest of the
e-commerce site owners, and it is here to stay. It is synching offline data and
online data together so that the retailers’ decision-making capacity may be
enhanced. In a nutshell, it allows retailers to understand the hidden consumer
patterns. The beauty of combining online and offline data from various channels
whether structured or unstructured at lightning speed is something which
retailers need in order to enhance decision making as it provides those hidden
consumer patterns which were never thought of.
10.
Micro-payments: Among the most revolutionary changes in the
coming months—not years—is the use of micro-payment systems from a variety of
financial firms, e.g., Paypal, Visa, WesternUnion, among others, including
banks. This trend is facilitated by the
W3C (World Wide Web Consortium) working group that approved these protocols and
technical standards for the interworking. These systems will change not only
how we carry money but how we value money and think about purchases. Payment
systems that make it easier to buy online, coupled with mobile technologies will
accelerate the usage of global e-commerce applications.
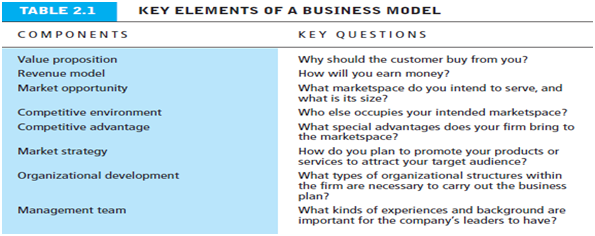


















Indiaedatasolutions offers Ecommerce Image Processing Services, As your eCommerce business expands ecommerce data entry Services, work progress updation on daily basis WordPress (Website) Outsource ecommerce Product Data entry services at lowest rates. http://www.indiaedatasolutions.com/product-image-editing-services/
ReplyDeleteWhy it’s important to check your credit score? getting your credit score is affordable
ReplyDeleteWonderful Contents.Thank you for sharing.Convenience products
ReplyDeleteSuperb article. It's very informative and useful for merchants who are looking for 2D Payment Gateway
ReplyDeleteor want to know more about 2D Payment
Superb article. It's very informative and useful for merchants who are looking for Retail Merchant Account or want to know more about Online Retail Merchant Account.
ReplyDelete
ReplyDeleteIn this post having more usefull information and improve our knowledge.Can you share more valuable information present Technology.
Thanks for great information you write it very clean. I am very lucky to get this tips from you.
Logistics Software
Fleet Management systemERP Software Companies
Manufacturing ERP
Human Resources Management Software
Nice blog, very interesting to read
ReplyDeleteI have bookmarked this article page as i received good information from this.
ERP Software in India | ERP Software Companies in India
Cloud Based ERP Software in India | ERP Software for Manufacturing Industries in India
thanks for the information nice blogs
ReplyDeletee commerce companies